Ron Auger sent an email to the [WASC Mail list] on some fine work presented recently by Microsoft Research. The paper (and accompanying PPT), titled [Pretty-Bad-Proxy: An Overlooked Adversary in Browsers’ HTTPS Deployments] is pretty cool and shows several techniques for a malicious inline proxy to sniff SSL sessions passing through the proxy. Its genuinely a bunch of cool findings and has been handled neatly (with the exception of some shocking clipart!).
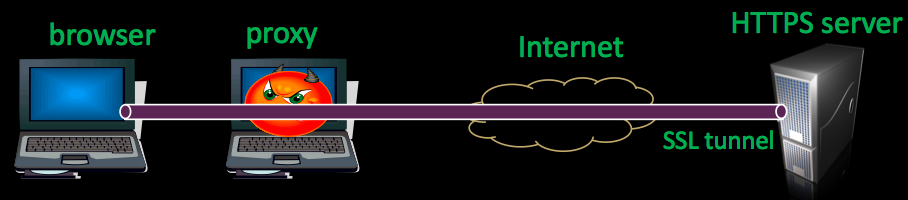
The attack logic is fairly simple. User tries to browse to https://mybank.com. The browser sends a connect message to the proxy. The proxy returns an HTTP 502 proxy error message. The magic comes in here. The browser interprets the returned 502 message within the security context of https://mybank.com.
So the attack works as follows:
- User tries to browse to https://mybank.com.
- Browser sends connect message to evil-proxy.
- Evil-proxy sends back a 502 message, with evil-Javascript and opens an iframe to https://mybank.com.
- Evil-proxy lets the request go to https://mybank.com and the page loads in the users browser.
- Evil-Javascript is now running in the same context as the banking session, so it has full access to page..
Elite!
With a little more arm bending the paper even goes on to remove the neccessity of full control of an evil proxy, relying on an attacker on the local network sniffing traffic and then racing the valid proxy server..
The findings have been disclosed to the browser vendors and have already been remediated, which means we can collectively breath a sigh of relief, but clearly, it has not been a good year for SSL (and SSL implementations).