Given the prevalence of Microsoft Active Directory domains as the primary means of managing large corporate networks both globally and in South Africa specifically; one of the common first goals of many internal penetration tests is to get Domain Administrator (DA) level access. To assist with this, a plethora of tools and techniques exist, from the initial “in” through to elevation of privilege and eventually extracting and cracking all domain credentials.
However, the processes followed are still manual and time consuming. This detracts from potentially more dangerous attacks that may be specific to the organisation under assessment. In particular, networks that require pivoting across several internal hosts results in an analyst engaging in sometimes time-consuming “lateral movement”.
Observing both the time consuming nature of these “common tasks” and that they appeared easily automatable, we decided to construct a framework for automating such activities; Automatic Domain Administrator & Network Exploitation (autoDANE) This framework orchestrates the industry’s currently favoured tools for Active Directory exploitation.
The goal for the project is to get DA rights as quickly as possible, relying on automation, so that analysts can start an internal assessment as a privileged user (or at least rule out the common approaches), rather than finishing as one. It is hoped, it will allow analysts to spend time on engagements emulating real life hacking scenarios, such as going after business critical applications instead of chasing DA.
The tool was originally released as a proof-of-concept at ZaCon 2015. After a lot of on-site testing, and getting feedback from some early adopters, it was reworked into an extensible framework, and released again at BSides Cape Town last Saturday.
The heart of the project is an event-driven task manager, which runs small plugins, normalizes their output, and passes that as input to other plugins based on predefined rules. For example, when a host is identified (either manually, or through running standard host enumeration techniques), the host’s net block is port scanned. Open ports are passed to other plugins, which run further fingerprinting or vulnerability scanning tasks.
Plugins are categorised as follows:
Host Enumeration
Plugins in this category run through standard techniques to quickly find hosts, such as assembling an initial scope based on the IP addresses of the DHCP assigned gateway and DNS resolvers, or trying to run a zone transfer against the Domain Controller,
Fingerprinting
These plugins look for useful information about hosts found in the first step. These do things such as portscanning hosts, saving host names, and taking screenshots and saving the HTML of websites for offline analysis.
Vulnerability Scanning
These check open ports identified in the fingerprinting phase for “low hanging fruit,” or simple vulnerabilities which can be exploited to get local command execution. The three bundled are common enough, and at least one instance is found nearly everywhere, but the list is nowhere near exhaustive, and will be expanded on over time. You can bring your own favourite exploit and feed it into the next step as an alternative.
Vulnerability Exploitation
These exploit vulnerabilities found in the previous phase, and gather as much information as possible from the hosts, such as impersonation tokens, local user hashes, credentials stored by the Windows Local Secret Authority, and credentials stored in memory. The primary focus of this phase is to collect credentials, however, you can always feed autoDANE your own creds if you prefer.
Currently, this is achieved by using the Metasploit Framework, however we’re looking at using ImPacket backed techniques in future.
Network Pivoting
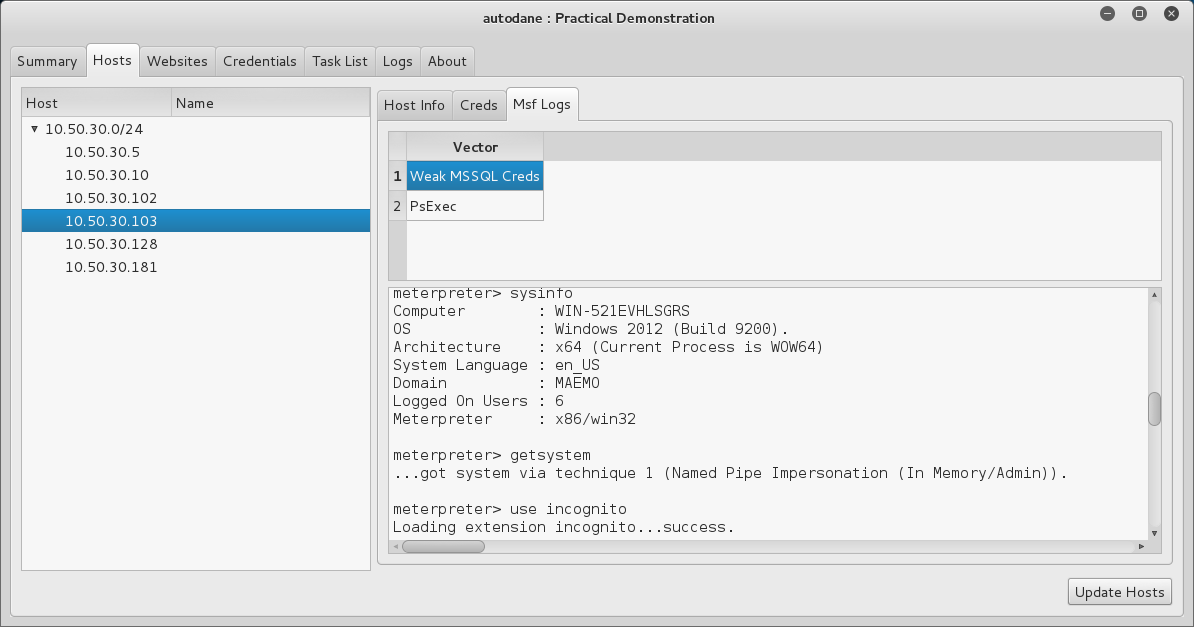
This section is the primary focus of the project. It takes both the local and domain credentials found on other hosts, and retries them across the footprint. When credentials are found to allow access to new hosts, Metasploit’s PsExec module is used to gather password hashes, credentials and impersonation tokens. New credentials are fed back into the process, and it is repeated until autoDANE has escalated itself as far as it can.
Running this blindly would run the risk of locking out domain accounts, so care is taken to prevent that. When domain accounts are pulled from memory, they’re verified by checking whether they can still log into the host where they were found before being tried anywhere else.
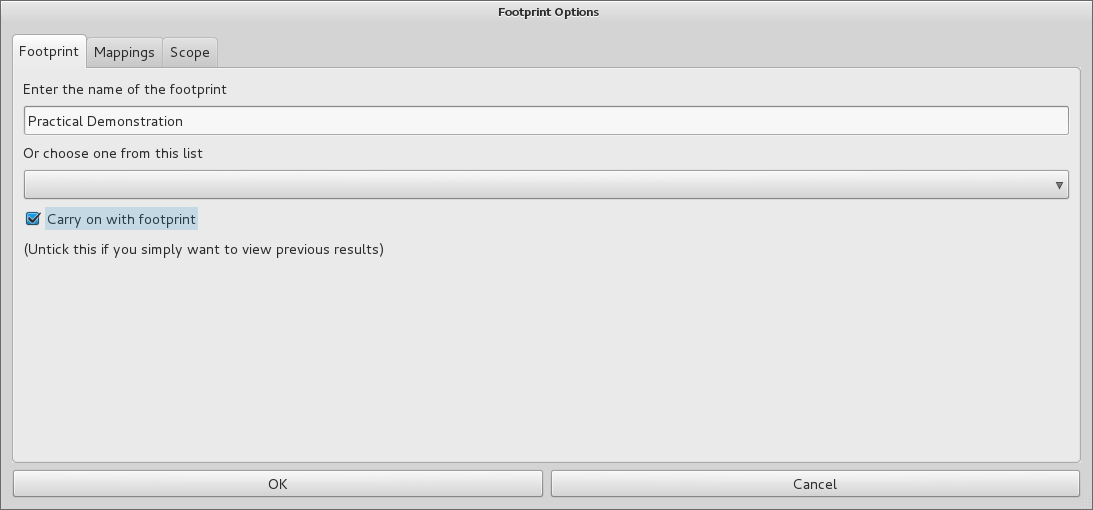
While the details can get quite technical, the entire process comes pre-configured. Running it is as simple as giving the scan a name:
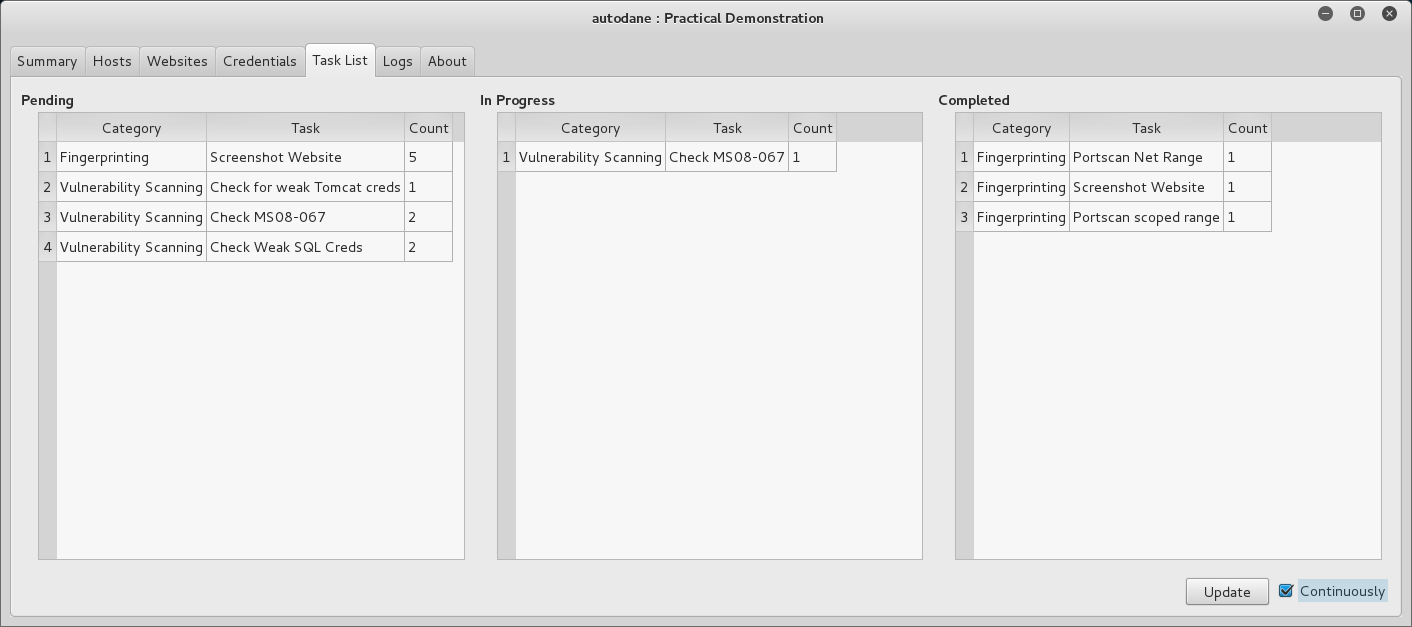
You can follow the scans progress by watching the Task List.
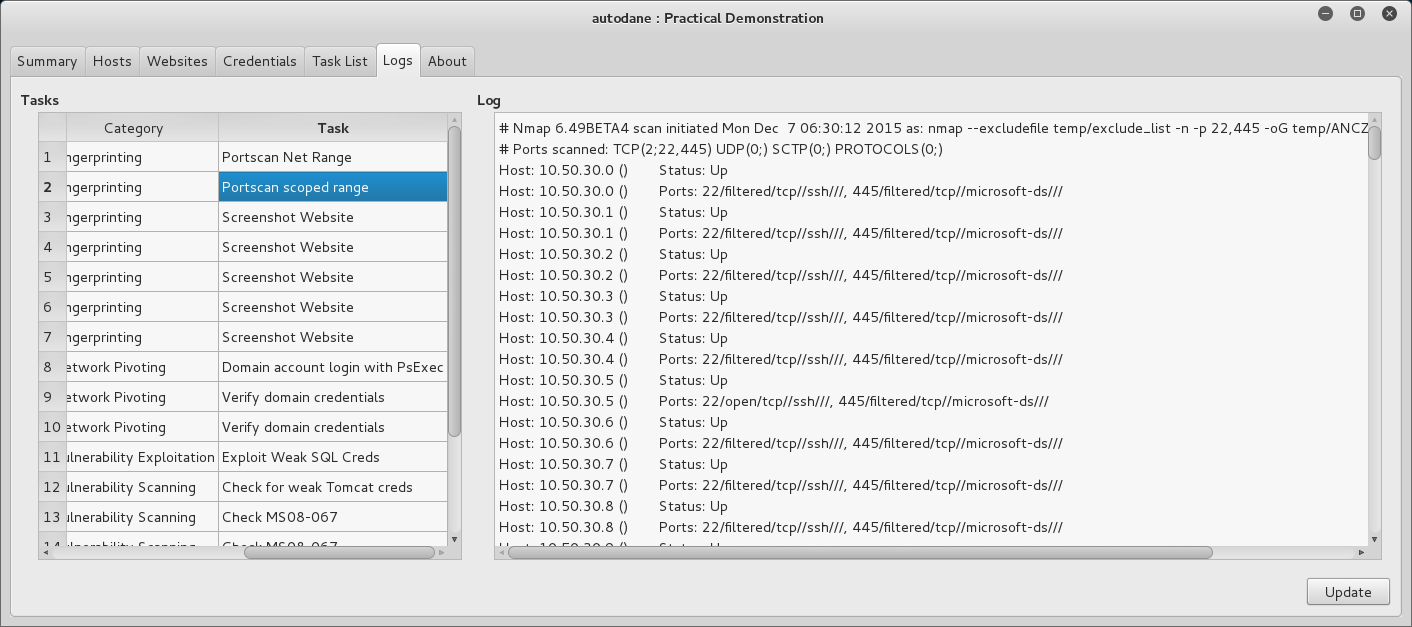
You can also see the raw output of each task by looking at the logs, you shouldn’t be guessing what it’s doing.
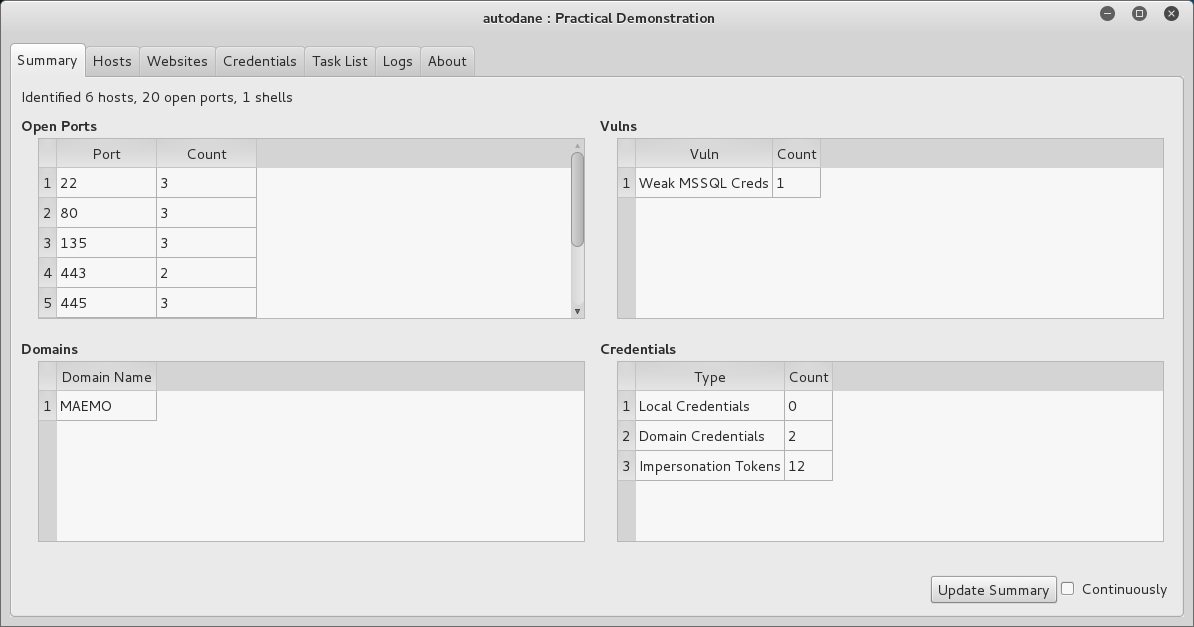
After the tool has been running for a while, you can view a summary of what it’s found:
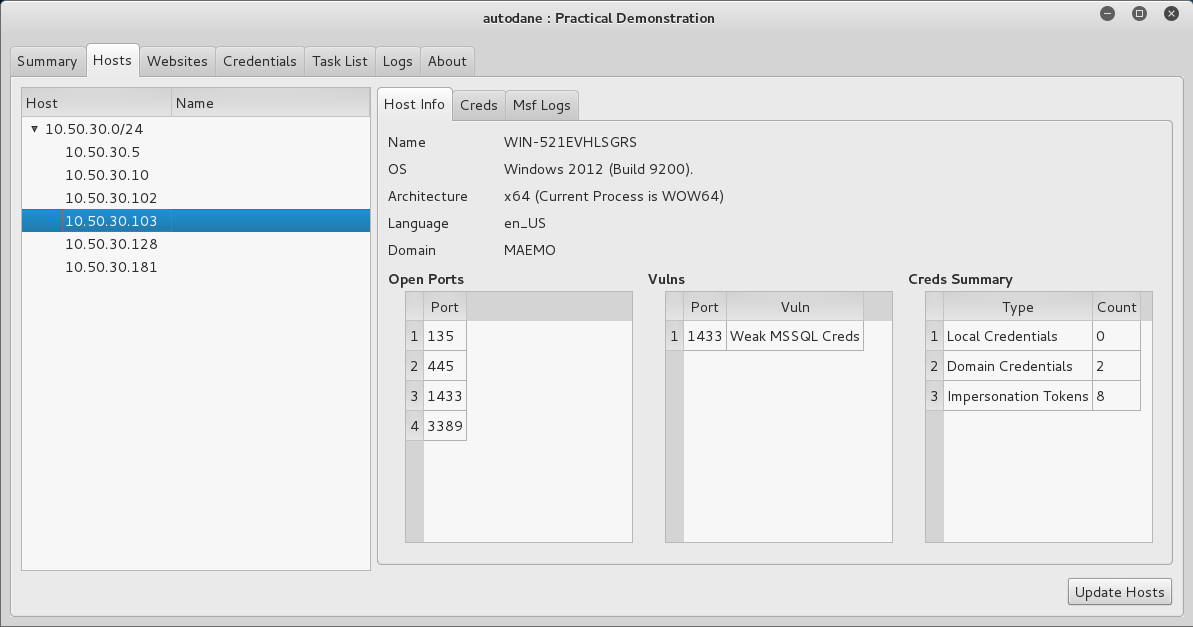
Host data is grouped logically.
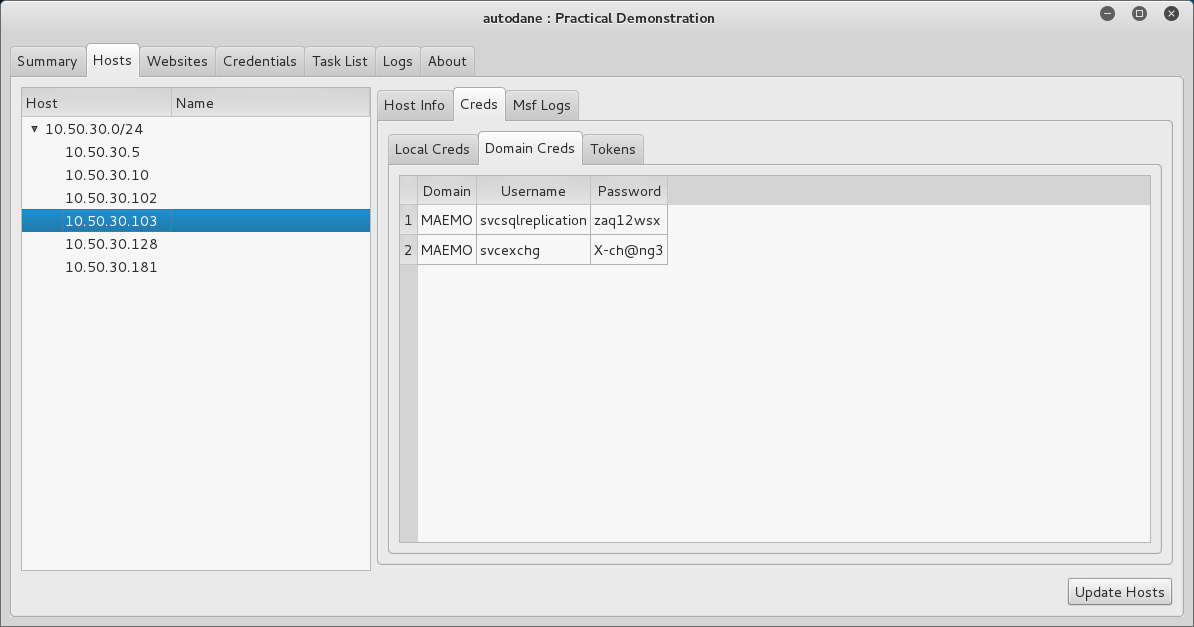
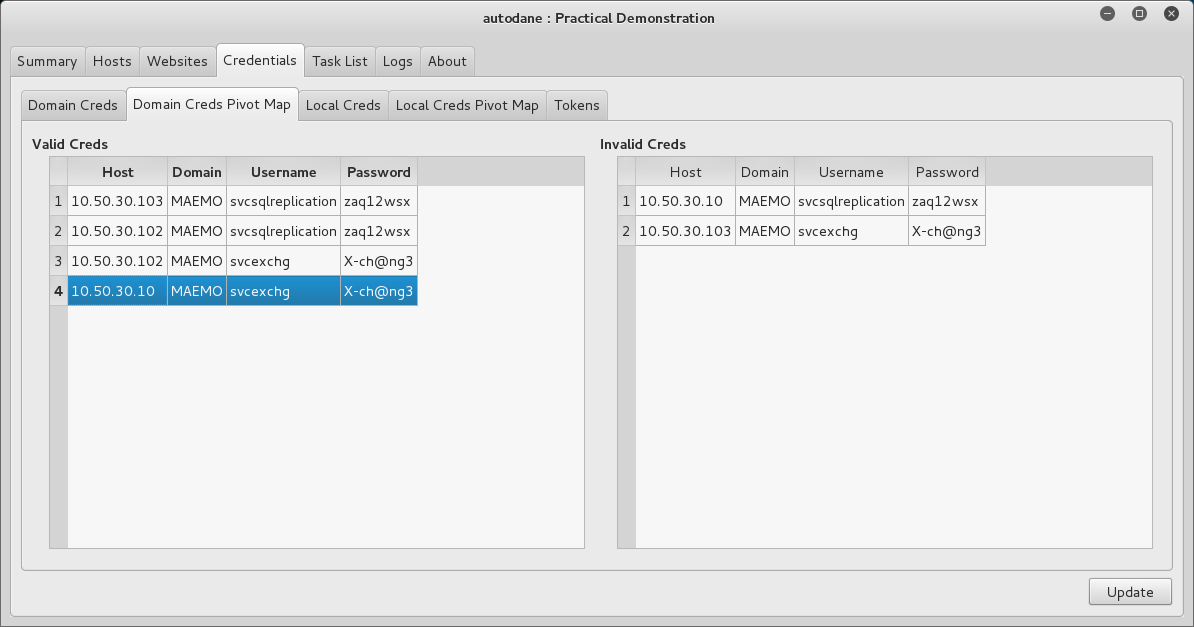
Together with valid credentials.
As well as exploit logs.
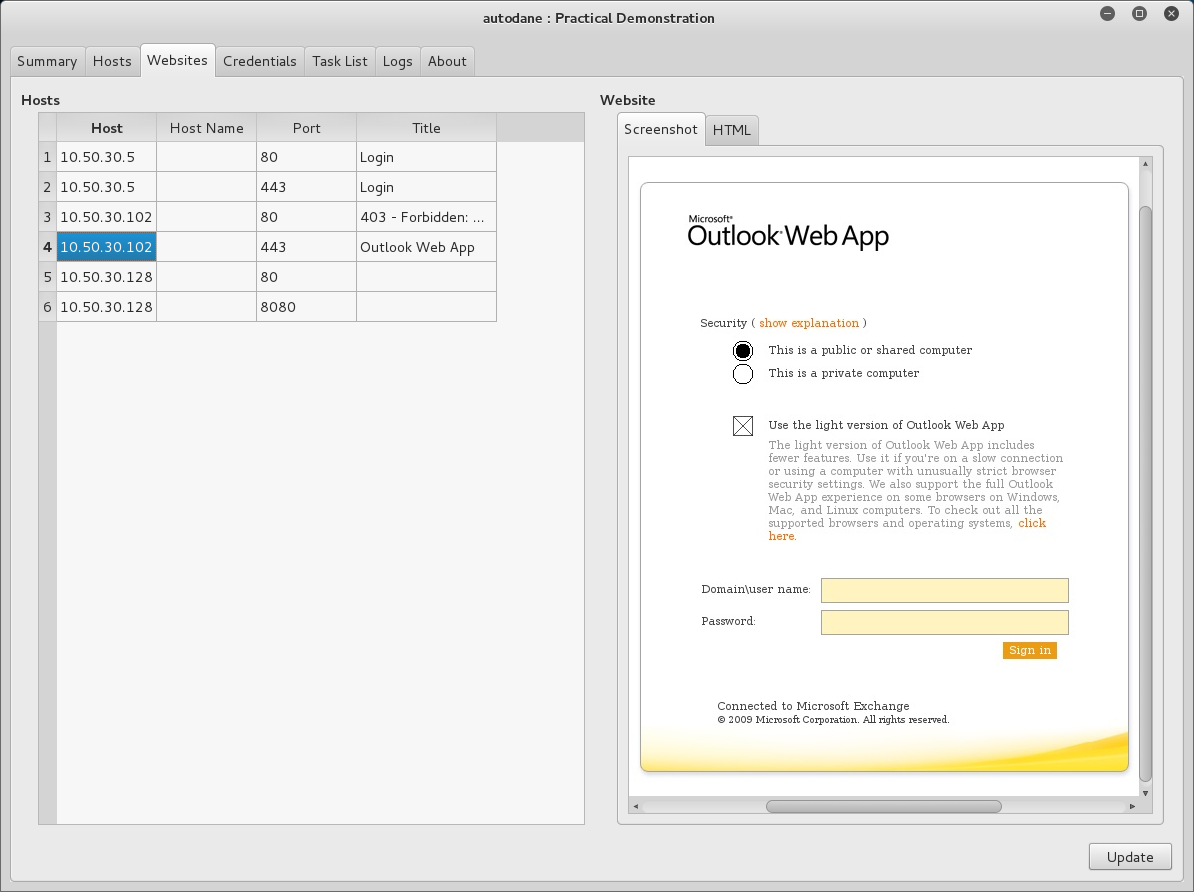
Websites are catalogued separately, so you can look through them for interesting business-related applications offline.
However, the real value comes from the Domain Credentials Map, which shows where different sets of credentials can be used. Ultimately, this will show you which credentials can log into various Domain Controllers.
To summarise, the project orchestrates the common tasks security analysts perform when on an internal security assessment. It makes use of the same tools, and applies the same techniques that are taught and used in the industry. This allows analysts to cover these relatively simple bases, while simultaneously going after business critical applications, and demonstrating other, more technically difficult avenues of attack.
If you’re keen to try the project, you can download it from SensePosts GitHub page here