Everyone has a mobile phone (ok some have two) and the wealth of information people put into them is staggering. This single platform gives attackers an incredibly large attack surface area to target, so it’s no surprise we *love* owning mobile devices.
With this in mind, the countdown to Blackhat USA has begun and we will be launching our latest iteration of the Mobile hacking course to the eager and thirsty minds that find themselves at the sensory circus that is Las Vegas!
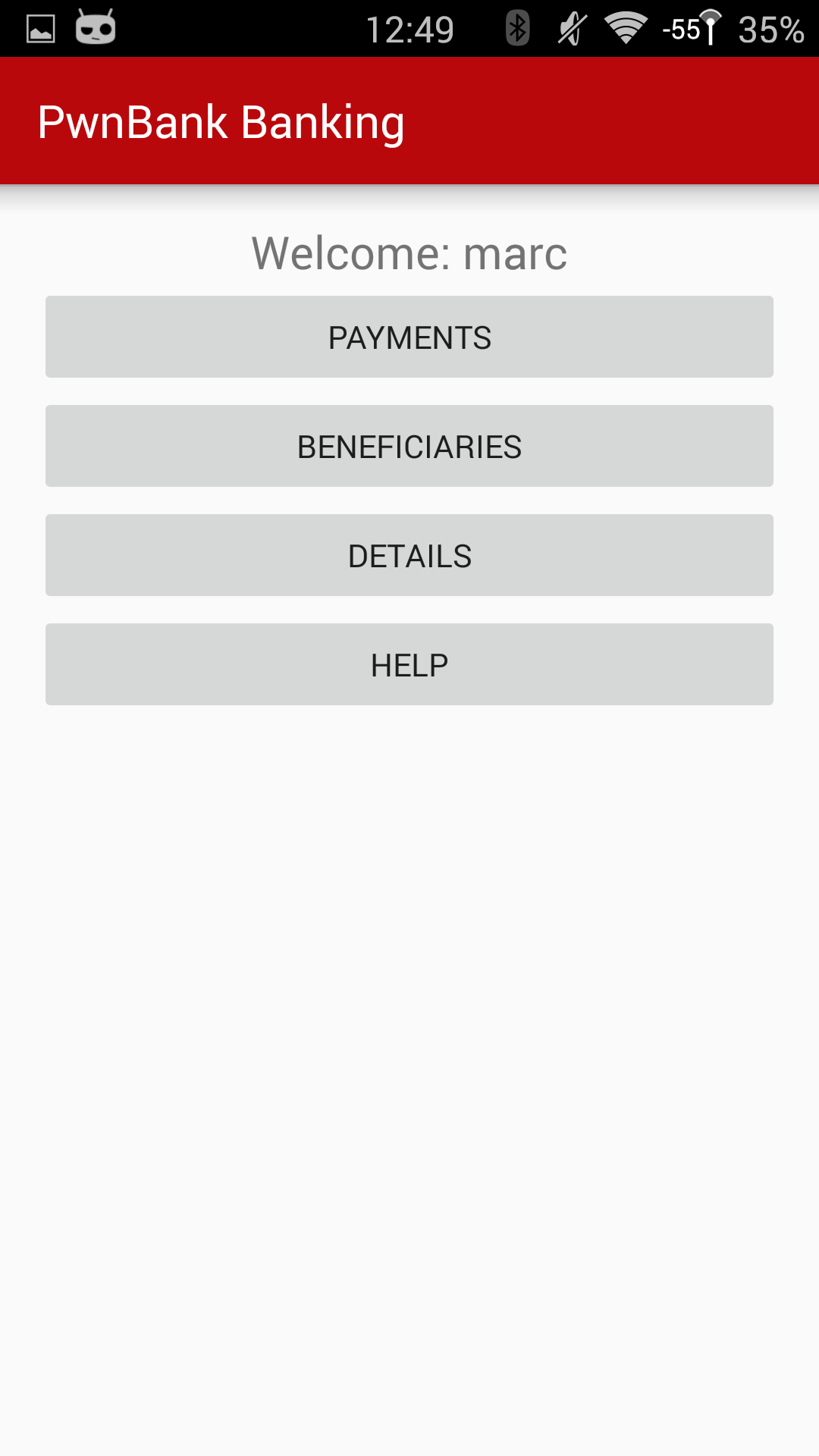
This iteration of the Mobile course will be the initial introduction of PwnBank. PwnBank is a fully-fledged financial banking application with all the usual “banking” functionality, such as managing payments, beneficiaries, etc. In addition, it has back-end services, which are also vulnerable to attack, so you get to own the entire network.
What’s new in this version?
Firstly the course is molded around a highly practical environment which sees students building and customizing their mobile workbench to understand how important it is to have a stable and effective workbench. This all takes place via utilizing customized bootable USB’s which takes away the pain and agony from Virtual Machines and introduces the speed and ease of using bootable USB’s.
During the course, you’ll be developing and building mobile applications in order to gain further insight into how to rip them apart. This drives home the principle of ” you can’t own what you can’t build” which isn’t 100% true but you can see the difference between someone who can and can’t build mobile applications and their corresponding pwnage.
Of course, building malicious mobile apps is never a bad thing, depending on who you ask ;)
Lifelike Targets
There’s nothing worse than a fake application riddled with easy vulnerabilities. Sure, you do get some in the wild but for the best part, mobile applications have been developed with a bit more robustness. Our response is for you to target a fictitious financial organization who just happened to release a mobile banking application. Students will be required to own the application in order to achieve their malicious goals, get rich and own the entire organization. What this means is that students will be required to use their newly acquired mobile haxoring foo to completely own the mobile application and use their mobile l00t to then compromise the organization and associated infrastructure.
Of course no good blog post is without screenshots, so here are some of Pwnbank itself.
One More Thing©
Finally, there’s something topical and juicy: ransomware. Once you’ve learned how to tear apart and assess mobile applications, we’ve picked out some of the real-life malicious ones found in the app stores for you to analyse.
How to Register
If the above sounds amazing (and indeed it should) and you want to register a place, head on over to Blackhat’s registration page and sign up.