With our recent release of BiDiBLAH 2.0, we’ve decided to revisit some real world scenarios, and ways BiDiBLAH can deal with it… Herewith, part 2. All the scenarios can be downloaded from the BiDiBLAH home page.
Scenario:
We have a class B network internally. Many of the users run FTP servers on their machines. We do not allow this – but how do I identify these machines?
Solution:
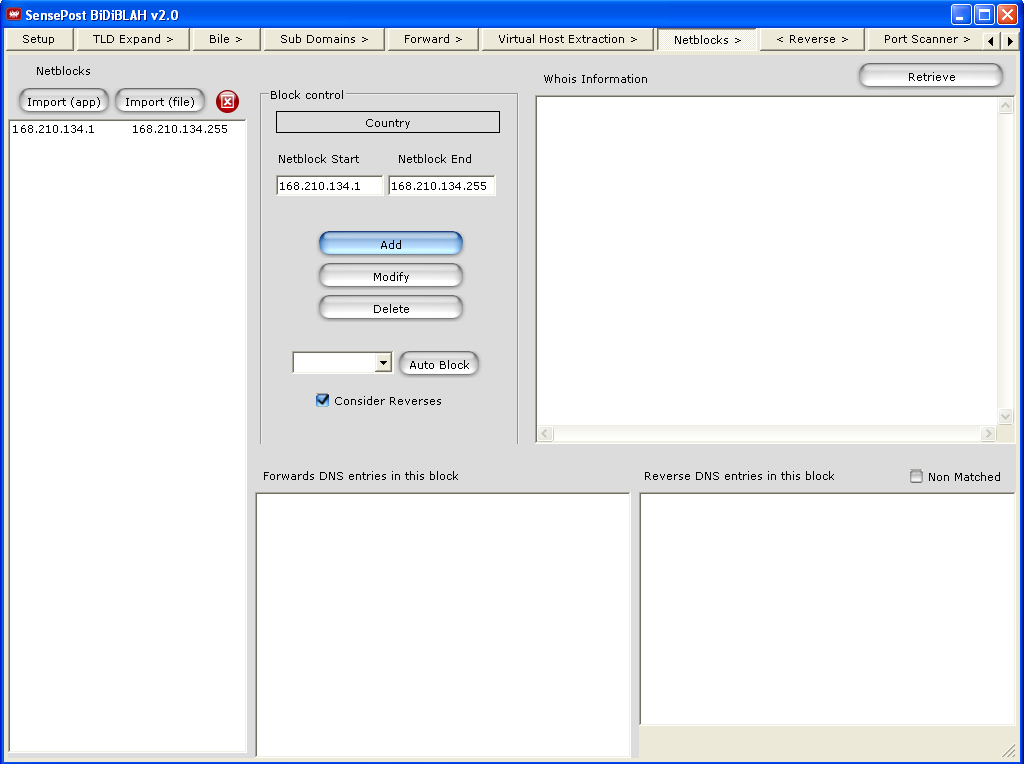
Using BiDiBLAH, define your network as netblocks.
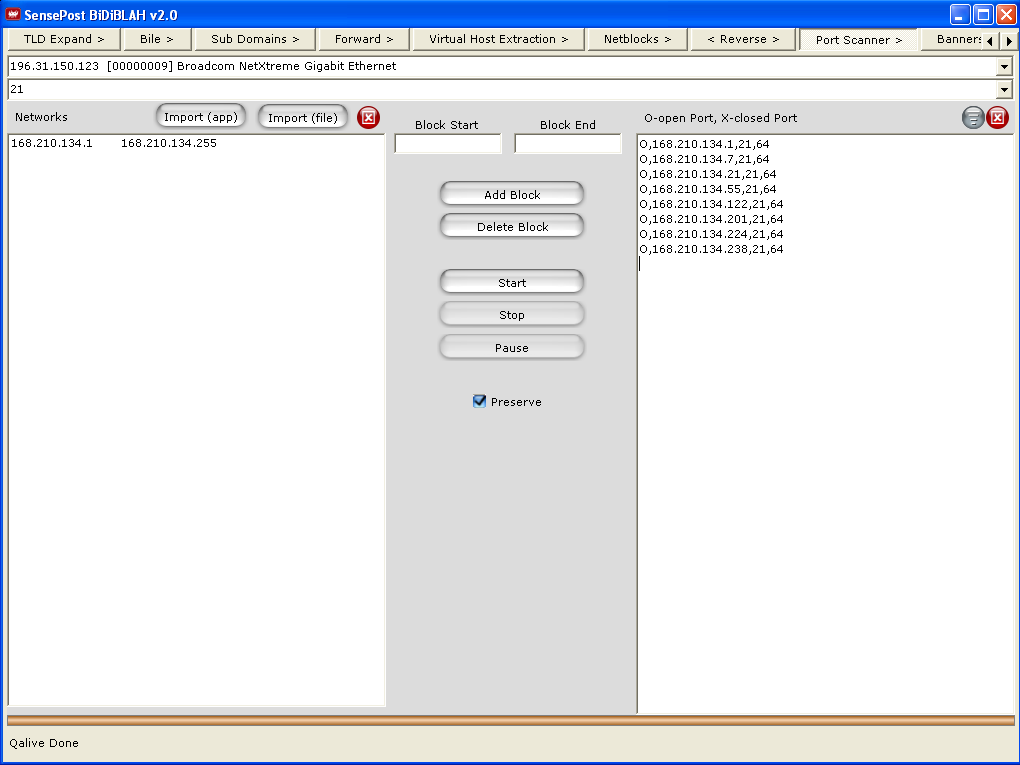
Next, perform a port scan for port 21/TCP (FTP)
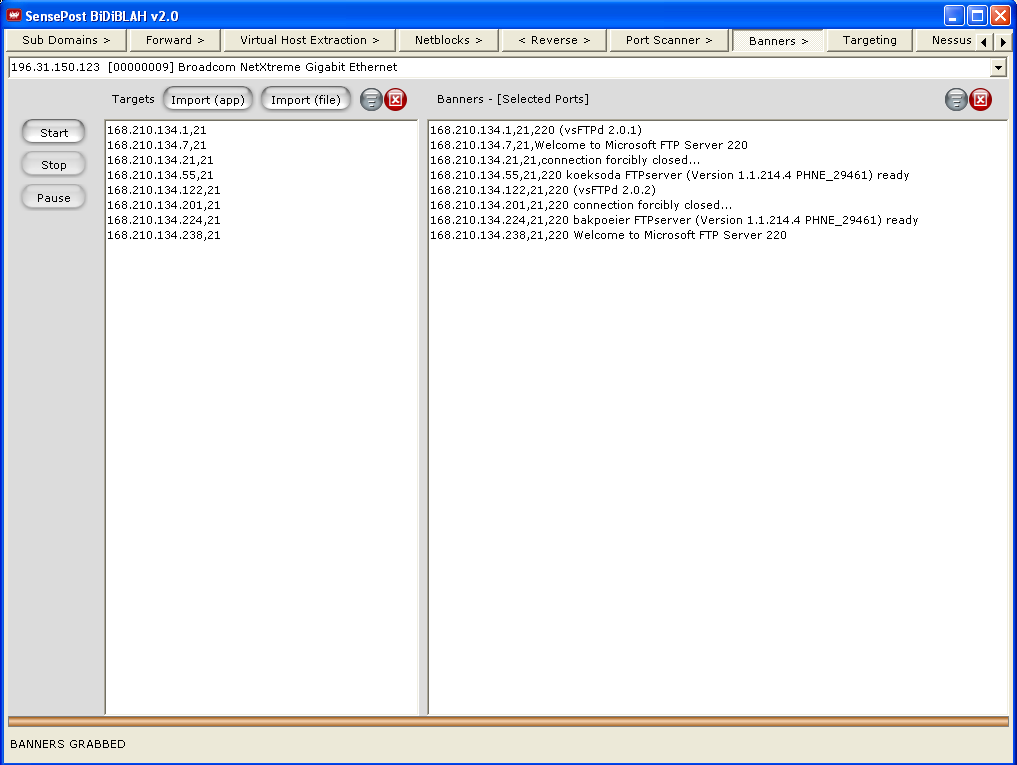
Extract the banners for the FTP servers found.
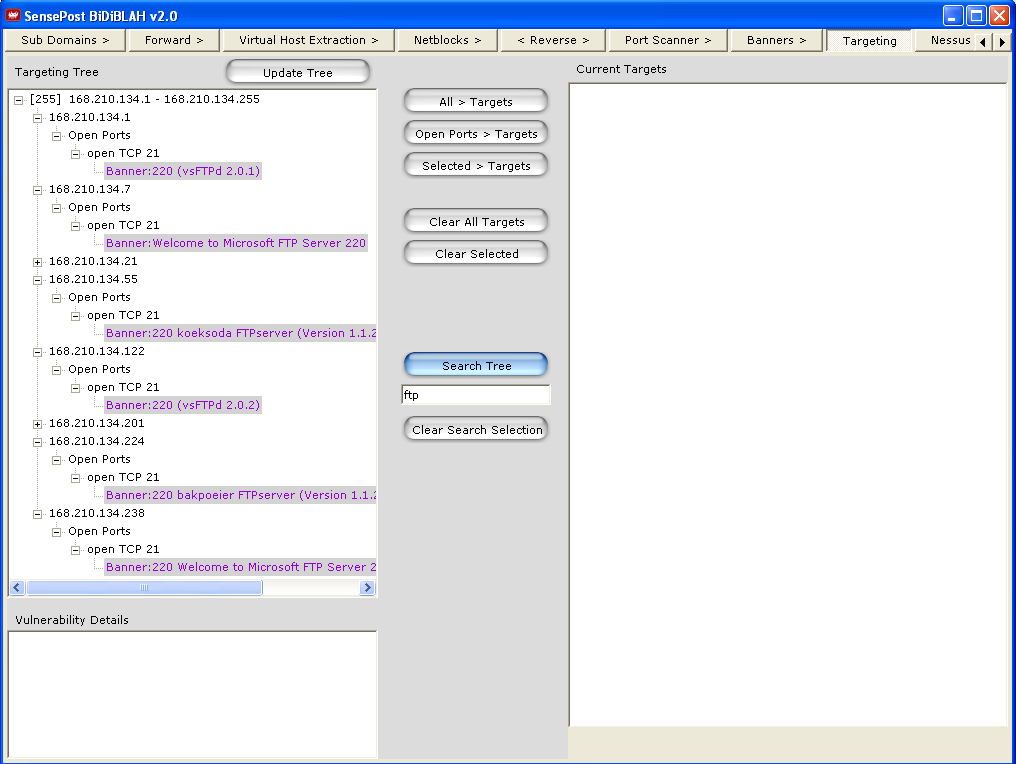
Go to the targeting tree, search for the version and collect the IP addresses.
/frankieg