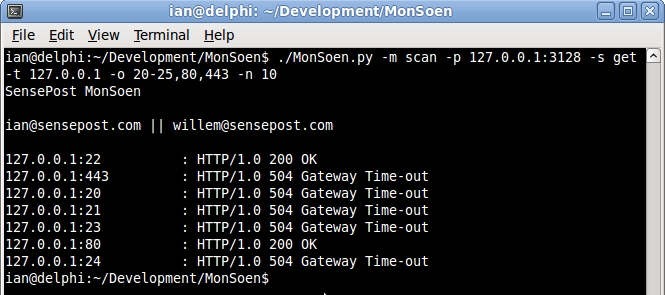
I was recently playing with a Wingate Proxy server, came across some arbitrary interestingness.
So, WinGate proxy includes a remote management agent which is accessed via a client utility called GateKeeper. This allows one to configure the WinGate server across the network. However, its not enabled to listen on the network by default, and only listens on 127.0.0.1:808. From my perusal of the documentation, the remote administrative facility should only be available to enterprise and professional license holders, and those firms using standard edition licenses will have to configure their proxy software locally.
In any case, WinGate proxy supports using CONNECT methods to negotiate connections for SSL-based web-sites etc, but no access control is in place to prevent users using this method to connect to 127.0.0.1:808. This, along with some python-fu, makes it a trivial task to access the remote administration service across the network. This is illustrated in the following images.
Naturally, after knocking together a little proxy tunnel script, I remembered an idea Gareth had a number of years ago for scanning networks and port ranges via badly configured proxies, and decided to incorporate them into the original tunnel script. An example is illustrated in the following image…
So, enter MonSoen.py. A cute (and probably entirely unnecessary) python-based script for tunnelling connections through proxy servers, scanning networks using GET or CONNECT and otherwise being miserable to others (nods at Gareth).
It’s going to need the python netaddr module. MonSoen is available from http://www.sensepost.com/research_misc.html
Ian.