As the need for online anonymity / privacy grew, the proxy industry flourished with many proxy owners generating passive incomes from their proxy networks.
Although ‘proxy’ is normally thought to imply some sort of daemonized application, such as Squid (or a SOCKS) daemon, the last couple of years have heralded in the age of CGI proxies and more commonly, their PHP variants.
These PHP proxies are extremely trivial to deploy and configure, especially since most hosting environments have PHP installed by default. When development of PHProxy (a popular PHP proxy) ceased, many devoted fans starting releasing their own customised PHProxy fixes and variants. In recent years, however, many proxy owners have gravitated towards Glype since it seemed to be well maintained (though the current status may be questionable).
While there have been tools created to portscan targets through SOCKS and HTTP proxies, I am not aware of any which reliably performed it through the current range of PHP proxies.
By default, Glype has few restrictions on what hosts / ports can be accessed through it and normally displays its cURL error messages as well. Using these apparent weaknesses, GlypeAhead is able to perform portscans of targets with reasonable accuracy.
It must be mentioned that even if a port is open on the target, it will be regarded as closed if the Glype proxy in use is unable to successfully connect to the service.
Due to GlypeAhead being a proof-of-concept tool, its logic has been purposefully limited to only work against Glype installations which display the default cURL error messages.
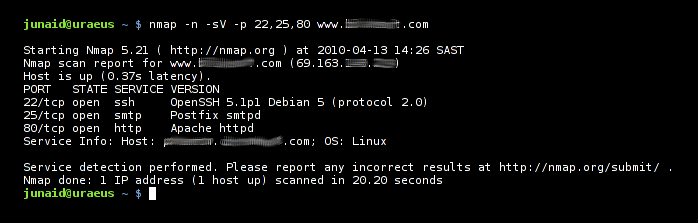
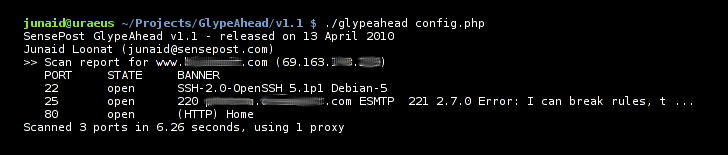
Below are screenshots of a Nmap scan compared to a GlypeAhead scan.
GlypeAhead is written in PHP (as is the Glype proxy), requires the cURL extension to be compiled with PHP, and is available from either our Tools section, or directly from here.