It is always a little bemusing to hear that we only provide pentests. Since 2001, SensePost has offered a very comprehensible vulnerability management service that’s evolved through multiple generations of technologies and methodologies into a service we’re very proud of. The Managed Vulnerability Scanning (“MVS”) service makes use of our purpose-built BroadView scanning technology to scan a number of high profile South African and European clients. More information can be found here, but the purpose of this post is to introduce it with a basic overview of its deployment.
To give you a better understanding of our coverage, below are a number of statistics from our scanning database.
Number of scans per week: 935 average per week
Number of findings stored: 3 795 963
Number of collected attribute instance: 1 274 016
Number of unique IPs listed as targets: 24723
Number of unique IPs with issues: 4931
However, the stats are not the interesting bit. BroadView goes further than simply storing open issues, it also tags interesting characteristics of the targets using ‘attributes’, which are pieces of information associated with a finding, but are not necessarily a result. It is possible to query these attributes and tie them back to hosts; this enables you to search across all hosts for matching attributes. The most used attributes are:
- TCP Banners
- Operating System Value
- Hosts Accessible (True/False)
- SMTP Relaying Allowed (True/False)
- SMB Directories
- CMS Type
With all these attributes, one can perform intelligent scanning or reporting. For example, target all Windows devices with an open port 80 and running IIS5, or show a list of all open relays on our domain, or keep an updated list that shows all BIND servers that still require the recent DoS patch. This can be very useful, especially when setting up targeted scans or for network/patch management. Effectively, the attributes allow you to utilize BroadView as a network service monitoring device rather than just a vulnerability scanner. BroadView makes use of a dashboard to display blizzards (widgets with specific data sets); the data source for the blizzards is anything we can pull from the vulnerability and attribute database, displayed as a list or graph. For this purpose we have specific widgets that can show you in an instant the open ports across your network, sensitive open ports such as database services or phpmywebadmin instances.
So, we have loads of data and it makes for interesting analysis.
For example:
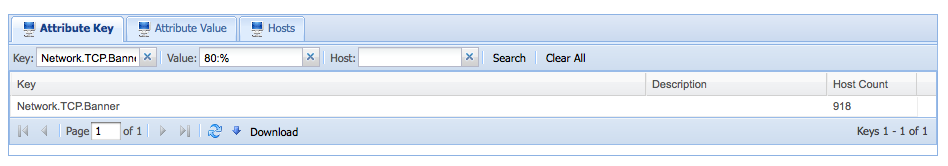
The number of targets with potential webservers: 918
And breaking it down further:
- Apache =186
- IIS = 303
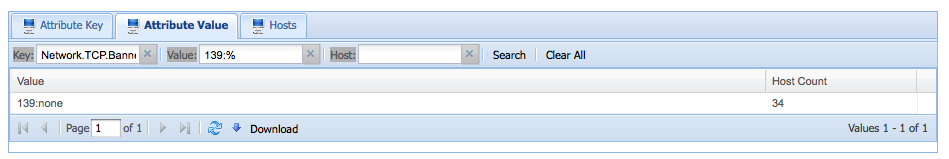
The number of targets inviting worm trouble: (port 139 open to the Internet)
The top 3 SSL certificate issuers used:
- Entrust – 230
- VeriSign – 159
- Thawte – 47
And many more.
Next time, more about the dashboard and the blizzards.