Introduction:
New types of mobile applications based on Trusted Execution Environments (TEE) and most notably ARM TrustZone micro-kernels are emerging which require new types of security assessment tools and techniques. In this blog post we review an example TrustZone application on a Galaxy S3 phone and demonstrate how to capture communication between the Android application and TrustZone OS using an instrumented version of the Mobicore Android library. We also present a security issue in the Mobicore kernel driver that could allow unauthorised communication between low privileged Android processes and Mobicore enabled kernel drivers such as an IPSEC driver.
Mobicore OS :
The Samsung Galaxy S III was the first mobile phone that utilized ARM TrustZone feature to host and run a secure micro-kernel on the application processor. This kernel named Mobicore is isolated from the handset’s Android operating system in the CPU design level. Mobicore is a micro-kernel developed by Giesecke & Devrient GmbH (G&D) which uses TrustZone security extension of ARM processors to create a secure program execution and data storage environment which sits next to the rich operating system (Android, Windows , iOS) of the Mobile phone or tablet. The following figure published by G&D demonstrates Mobicore’s architecture :
 Overview of Mobicore (courtesy of G&D)
Overview of Mobicore (courtesy of G&D)
A TrustZone enabled processor provides “Hardware level Isolation” of the above “Normal World” (NWd) and “Secure World” (SWd) , meaning that the “Secure World” OS (Mobicore) and programs running on top of it are immune against software attacks from the “Normal World” as well as wide range of hardware attacks on the chip. This forms a “trusted execution environment” (TEE) for security critical application such as digital wallets, electronic IDs, Digital Rights Management and etc. The non-critical part of those applications such as the user interface can run in the “Normal World” operating system while the critical code, private encryption keys and sensitive I/O operations such as “PIN code entry by user” are handled by the “Secure World”. By doing so, the application and its sensitive data would be protected against unauthorized access even if the “Normal World” operating system was fully compromised by the attacker, as he wouldn’t be able to gain access to the critical part of the application which is running in the secure world.
Mobicore API:
The security critical applications that run inside Mobicore OS are referred to as trustlets and are developed by third-parties such as banks and content providers. The trustlet software development kit includes library files to develop, test and deploy trustlets as well as Android applications that communicate with relevant trustlets via Mobicore API for Android. Trustlets need to be encrypted, digitally signed and then remotely provisioned by G&D on the target mobile phone(s). Mobicore API for Android consists of the following 3 components:
1) Mobicore client library located at /system/lib/libMcClient.so: This is the library file used by Android OS or Dalvik applications to establish communication sessions with trustlets on the secure world
2) Mobicore Daemon located at /system/bin/mcDriverDaemon: This service proxies Mobicore commands and responses between NWd and SWd via Mobicore device driver
3) Mobicore device driver: Registers /dev/mobicore device and performs ARM Secure Monitor Calls (SMC) to switch the context from NWd to SWd
The source code for the above components can be downloaded from Google Code. I enabled the verbose debug messages in the kernel driver and recompiled a Samsung S3 kernel image for the purpose of this analysis. Please note that you need to download the relevant kernel source tree and stock ROM for your S3 phone kernel build number which can be found in “Settings->About device”. After compiling the new zImage file, you would need to insert it into a custom ROM and flash your phone. To build the custom ROM I used “Android ROM Kitchen 0.217” which has the option to unpack zImage from the stock ROM, replace it with the newly compiled zImage and pack it again.
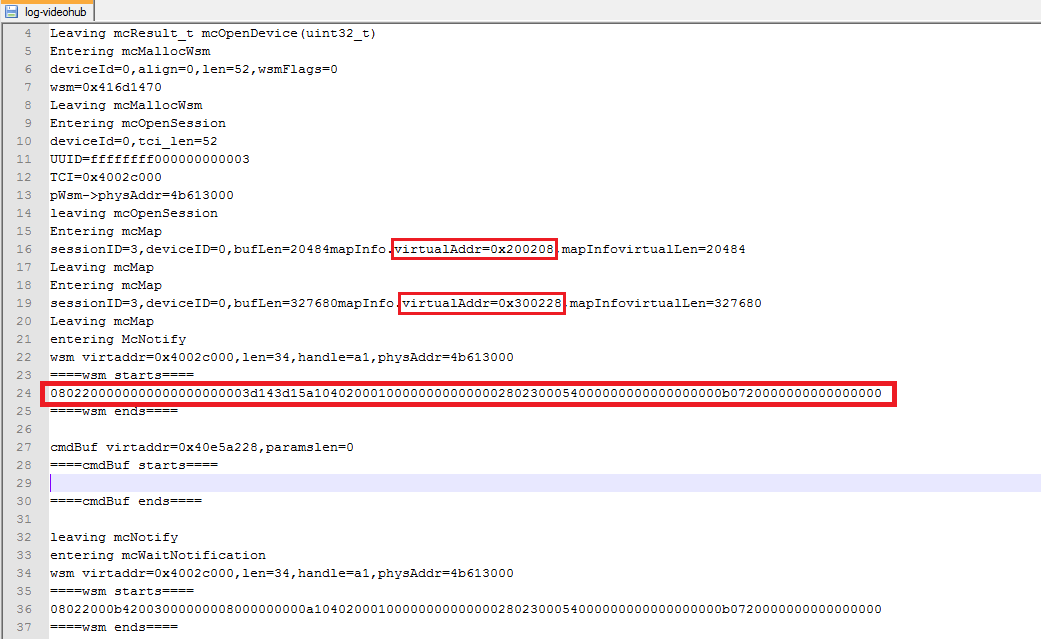
By studying the source code of the user API library and observing debug messages from the kernel driver, I figured out the following data flow between the android OS and Mobicore to establish a session and communicate with a trustlet:
1) Android application calls mcOpenDevice() API which cause the Mobicore Daemon (/system/bin/mcDriverDaemon) to open a handle to /dev/mobicore misc device.
2) It then allocates a “Worlds share memory” (WSM) buffer by calling mcMallocWsm() that cause the Mobicore kernel driver to allocate wsm buffer with the requested size and map it to the user space application process. This shared memory buffer would later be used by the android application and trustlet to exchange commands and responses.
3) The mcOpenSession() is called with the UUID of the target trustlet (10 bytes value, for instance : ffffffff000000000003 for PlayReady DRM truslet) and allocate wsm address to establish a session with the target trustlet through the allocated shared memory.
4) Android applications have the option to attach additional memory buffers (up to 6 with maximum size of 1MB each) to the established session by calling mcMap() API. In case of PlayReady DRM trustlet which is used by the Samsung VideoHub application, two additional buffers are attached: one for sending and receiving the parameters and the other for receiving trustlet’s text output.
5) The application copies the command and parameter types to the WSM along with the parameter values in second allocated buffer and then calls mcNotify() API to notify the Mobicore that a pending command is waiting in the WSM to be dispatched to the target trustlet.
6) The mcWaitNotification() API is called with the timeout value which blocks until a response received from the trustlet. If the response was not an error, the application can read trustlets’ returned data, output text and parameter values from WSM and the two additional mapped buffers.
7) At the end of the session the application calls mcUnMap, mcFreeWsm and mcCloseSession .
The Mobicore kernel driver is the only component in the android operating system that interacts directly with Mobicore OS by use of ARM CPU’s SMC instruction and Secure Interrupts . The interrupt number registered by Mobicore kernel driver in Samsung S3 phone is 47 that could be different for other phone or tablet boards. The Mobicore OS uses the same interrupt to notify the kernel driver in android OS when it writes back data.
Analysis of a Mobicore session:
There are currently 5 trustlets pre-loaded on the European S3 phones as listed below:
shell@android:/ # ls /data/app/mcRegistry
00060308060501020000000000000000.tlbin
02010000080300030000000000000000.tlbin
07010000000000000000000000000000.tlbin
ffffffff000000000000000000000003.tlbin
ffffffff000000000000000000000004.tlbin
ffffffff000000000000000000000005.tlbin
The 07010000000000000000000000000000.tlbin is the “Content Management” trustlet which is used by G&D to install/update other trustlets on the target phones. The 00060308060501020000000000000000.tlbin and ffffffff000000000000000000000003.tlbin are DRM related truslets developed by Discretix. I chose to analyze PlayReady DRM trustlet (ffffffff000000000000000000000003.tlbin), as it was used by the Samsung videohub application which is pre-loaded on the European S3 phones.
The videohub application dose not directly communicate with PlayReady trustlet. Instead, the Android DRM manager loads several DRM plugins including libdxdrmframeworkplugin.so which is dependent on libDxDrmServer.so library that makes Mobicore API calls. Both of these libraries are closed source and I had to perform dynamic analysis to monitor communication between libDxDrmServer.so and PlayReady trustlet. For this purpose, I could install API hooks in android DRM manager process (drmserver) and record the parameter values passed to Mobicore user library (/system/lib/libMcClient.so) by setting LD_PRELOAD environment variable in the init.rc script and flash my phone with the new ROM. I found this approach unnecessary, as the source code for Mobicore user library was available and I could add simple instrumentation code to it which saves API calls and related world shared memory buffers to a log file. In order to compile such modified Mobicore library, you would need to the place it under the Android source code tree on a 64 bit machine (Android 4.1.1 requires 64 bit machine to compile) with 30 GB disk space. To save you from this trouble, you can download a copy of my Mobicore user library from here. You need to create the empty log file at /data/local/tmp/log and replace this instrumented library with the original file (DO NOT FORGET TO BACKUP THE ORIGINAL FILE). If you reboot the phone, the Mobicore session between Android’s DRM server and PlayReady trustlet will be logged into /data/local/tmp/log. A sample of such session log is shown below:
The content and address of the shared world memory and two additional mapped buffers are recorded in the above file. The command/response format in wsm buffer is very similar to APDU communication in smart card applications and this is not a surprise, as G&D has a long history in smart card technology. The next step is to interpret the command/response data, so that we can manipulate them later and observe the trustlet behavior. The trustlet’s output in text format together with inspecting the assembly code of libDxDrmServer.so helped me to figure out the PlayReady trustlet command and response format as follows:
client command (wsm) : 08022000b420030000000001000000002500000028023000300000000500000000000000000000000000b0720000000000000000
client parameters (mapped buffer 1): 8f248d7e3f97ee551b9d3b0504ae535e45e99593efecd6175e15f7bdfd3f5012e603d6459066cc5c602cf3c9bf0f705b
trustlet response (wsm):08022000b420030000000081000000002500000028023000300000000500000000000000000000000000b0720000000000000000
trustltlet text output (mapped buffer 2):
==================================================
SRVXInvokeCommand command 1000000 hSession=320b4
SRVXInvokeCommand. command = 0x1000000 nParamTypes=0x25
SERVICE_DRM_BBX_SetKeyToOemContext – pPrdyServiceGlobalContext is 32074
SERVICE_DRM_BBX_SetKeyToOemContext cbKey=48
SERVICE_DRM_BBX_SetKeyToOemContext type=5
SERVICE_DRM_BBX_SetKeyToOemContext iExpectedSize match real size=48
SERVICE_DRM_BBX_SetKeyToOemContext preparing local buffer DxDecryptAsset start – iDatatLen=32, pszInData=0x4ddf4 pszIntegrity=0x4dde4
DxDecryptAsset calling Oem_Aes_SetKey DxDecryptAsset
calling DRM_Aes_CtrProcessData DxDecryptAsset
calling DRM_HMAC_CreateMAC iDatatLen=32 DxDecryptAsset
after calling DRM_HMAC_CreateMAC DxDecryptAsset
END SERVICE_DRM_BBX_SetKeyToOemContext
calling DRM_BBX_SetKeyToOemContext
SRVXInvokeCommand.id=0x1000000 res=0x0
==============================================
By mapping the information disclosed in the trustlet text output to the client command the following format was derived:
08022000 : virtual memory address of the text output buffer in the secure world (little endian format of 0x200208)
b4200300 : PlayReady session ID
00000001: Command ID (0x1000000)
00000000: Error code (0x0 = no error, is set by truslet after mcWaitNotification)
25000000: Parameter type (0x25)
28023000: virtual memory address of the parameters buffer in the secure world (little endian format of 0x300228)
30000000: Parameters length in bytes (0x30, encrypted key length)
05000000: encryption key type (0x5)
The trustlet receives client supplied memory addresses as input data which could be manipulated by an attacker. We’ll test this attack later. The captured PlayReady session involved 18 command/response pairs that correspond to the following high level diagram of PlayReady DRM algorithm published by G&D. I couldn’t find more detailed specification of the PlayReady DRM on the MSDN or other web sites. But at this stage, I was not interested in the implementation details of the PlayReady schema, as I didn’t want to attack the DRM itself, but wanted to find any exploitable issue such as a buffer overflow or memory disclosure in the trustlet.
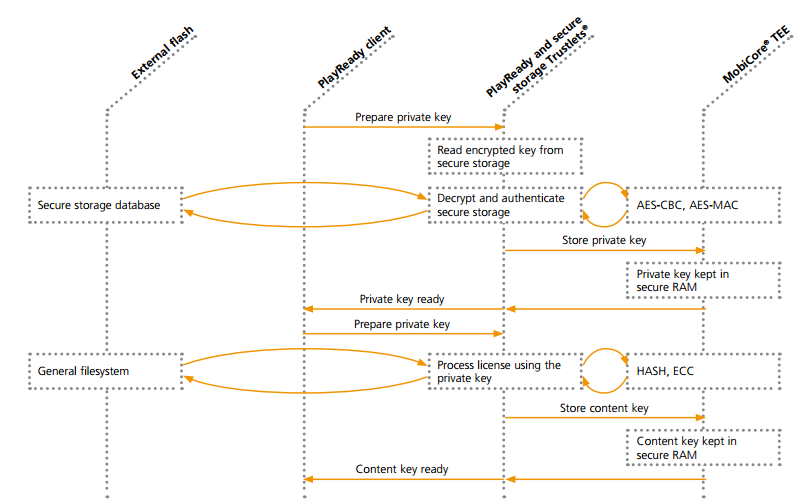 DRM Trustlet diagram (courtesy of G&D)
DRM Trustlet diagram (courtesy of G&D)
Security Tests:
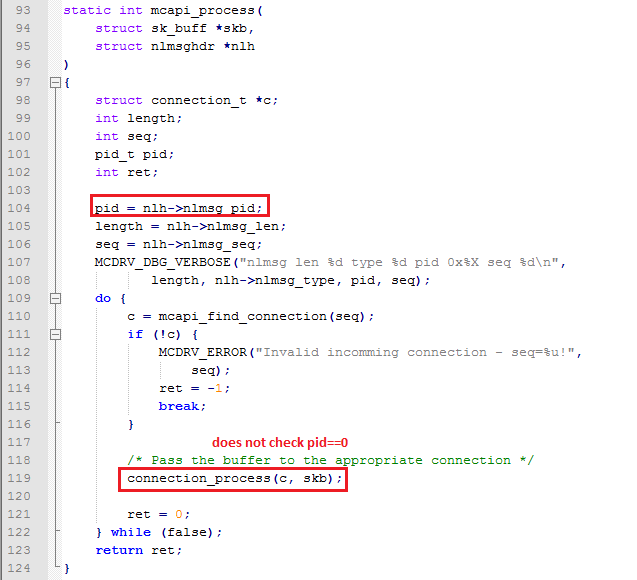
I started by auditing the Mobicore daemon and kernel driver source code in order to find issues that can be exploited by an android application to attack other applications or result in code execution in the Android kernel space. I find one issue in the Mobicore kernel API which is designed to provide Mobicore services to other Android kernel components such as an IPSEC driver. The Mobicore driver registers Linux netLink server with id=17 which was intended to be called from the kernel space, however a Linux user space process can create a spoofed message using NETLINK sockets and send it to the Mobicore kernel driver netlink listener which as shown in the following figure did not check the PID of the calling process and as a result, any Android app could call Mobicore APIs with spoofed session IDs. The vulnerable code snippet from MobiCoreKernelApi/main.c is included below.
An attacker would need to know the “sequence number” of an already established netlink connection between a kernel component such as IPSEC and Mobicore driver in order to exploit this vulnerability. This sequence numbers were incremental starting from zero but currently there is no kernel component on the Samsung phone that uses the Mobicore API, thus this issue was not a high risk. We notified the vendor about this issue 6 months ago but haven’t received any response regarding the planned fix. The following figures demonstrate exploitation of this issue from an Android unprivileged process :
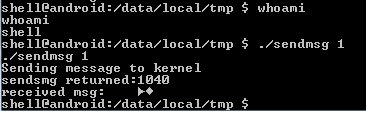 Netlink message (seq=1) sent to Mobicore kernel driver from a low privileged process
Netlink message (seq=1) sent to Mobicore kernel driver from a low privileged process
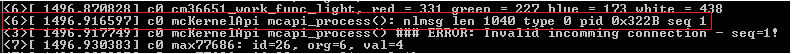 Unauthorised netlink message being processed by the Mobicore kernel driver
Unauthorised netlink message being processed by the Mobicore kernel driver
In the next phase of my tests, I focused on fuzzing the PlayReady DRM trustlet that mentioned in the previous section by writing simple C programs which were linked with libMcClient.so and manipulating the DWORD values such as shared buffer virtual address. The following table summarises the results:
| wsm offset | Description | Results |
| 0 | Memory address of the mapped output buffer in trustlet process (original value=0x08022000) | for values<0x8022000 the fuzzer crashed
values >0x8022000 no errors |
| 41 | memory address of the parameter mapped buffer in trusltet process (original value=0x28023000) | 0x00001000<value<0x28023000 the fuzzer crashed
value>=00001000 trustlet exits with “parameter refers to secure memory area” value>0x28023000 no errors |
| 49 | Parameter length (encryption key or certificate file length) | For large numbers the trustlet exits with “malloc() failed” message |
The fuzzer crash indicated that Mobicore micro-kernel writes memory addresses in the normal world beyond the shared memory buffer which was not a critical security issue, because it means that fuzzer can only attack itself and not other processes. The “parameter refers to secure memory area” message suggests that there is some sort of input validation implemented in the Mobicore OS or DRM trustlet that prevents normal world’s access to mapped addresses other than shared buffers. I haven’t yet run fuzzing on the parameter values itself such as manipulating PlayReady XML data elements sent from the client to the trustlet. However, there might be vulnerabilities in the PlayReady implementation that can be picked up by smarter fuzzing.
Conclusion:
We demonstrated that intercepting and manipulating the worlds share memory (WSM) data can be used to gain better knowledge about the internal workings of Mobicore trustlets. We believe that this method can be combined with the side channel measurements to perform blackbox security assessment of the mobile TEE applications. The context switching and memory sharing between normal and secure world could be subjected to side channel attacks in specific cases and we are focusing our future research on this area.