When we finally decided on a date, sensecon 2020 was little over a month away. Unlike our public client events, internally sensecon is a three day conference filled with trainings, a hackathon and a ton of fun. Traditionally we would have had the hackathon in person, but this year our only option was to do it remotely. Overall we had a blast, both in the preparation phase but also during the conference. It was the largest one we had to date, consisting of over 120 Orange Cyberdefense hackers from 8 countries around the globe! This blog post will be a reflection on these three days filled with incredibly exciting hacks, talking about how we got there, how it went and what we had learned along the way. All while I recover from a little sleep deprivation.
preparation
We set two goals for sensecon which was used to both determine what we focus on during the con and as a measurement for success afterwards. Those were: make a new friend & learn something new.
With online conferences being the norm this year, and our significantly larger number of hackers that would participate when compared to previous years, we went with Discord as the platform where we would run it. DEF CON 28 had a successful “Safe Mode” conference using Discord, and I figured the platform had more than proven its worth by now. As a backup we had Teams ready in case we needed it.
Any activities we planned had to be considerate of the fact that we spanned across three, predominantly European, timezones. Thanks to DST I double checked my timing a few times too!
Our final schedule meant that we released two challenges before the conference on the 2nd of November, with the conference itself running from the 5th to the 7th of November.
hackers! hackers everywhere
Towards the end of the conference we had over 120 hackers join the Discord server, with a peak online count being just under a hundred. As far as county representation goes, the following countries were all part of the hackathon; Sweden, Belgium, The Netherlands, France, Norway, Morocco, United Kingdom and South Africa.
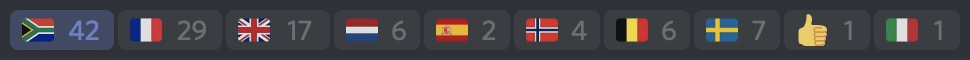
The privilege to interact with such a diverse crowd is quite something.
training
We ran four training classes on the Thursday, delivered by Hector, Sergio, Paul and Jameel. Hector gave an introduction to CodeQL, bootstrapping attendees to both recreate existing queries used to find real world vulnerabilities (such as CVE-2017-9805), as well as enabling them to write their own. Sergio gave a class covering numerous Active Directory attacks, including topics such as Kerberos, Resource-based Constrained Delegation, Discretionary Access Control List and their appropriate abuse scenarios. Paul’s workshop focused on Windows-specific privilege escalation and persistence techniques, diving into Access Control Entries, Access Tokens, writing your own DLL’s and other exploits such as CVE-2020-16938. Finally, Jameel delivered an eBPF workshop, unveiling the various capabilities that eBPF offers, one-liner tools to attach to kernel probes and other custom programs that could be written to instrument various parts of the Linux operating system.
We quickly filled the 50-person stream limit on Discord (which as you would expect resulted in a bit of a panic), but thankfully this wasn’t too big of a deal as the classes were mostly evenly spread. In retrospect (and something we changed mid-conference), broadcasting to larger audiences instead of smaller groups is just better done using something like Zoom.
challenges
We had three challenges in total. A password challenge, a programming challenge and a Discord bot challenge. We did not officially announce the Discord challenge, with the hope that folks would discover it on their own (oh and they did!). The challenges were released a week before the conference, primarily to give people ample time to play with them, but also to help keep the focus on the hackathon when it was time.
All of the challenges we built will be open sourced soon!
password challenge
Primarily the brainchild of Szymon, interactions with the password challenge was implemented in the Discord bot. Using a set of commands, you could download one of four challenges that contained hashes for you to crack and submit your clears again.
Each successful clear submitted netted you a bunch of points, applying a minor decay to the total points you could score to help with a tie breaker. Periodically, statistics were submitted to the password challenge channel, keeping everyone on their toes as far as the leaderboard goes.
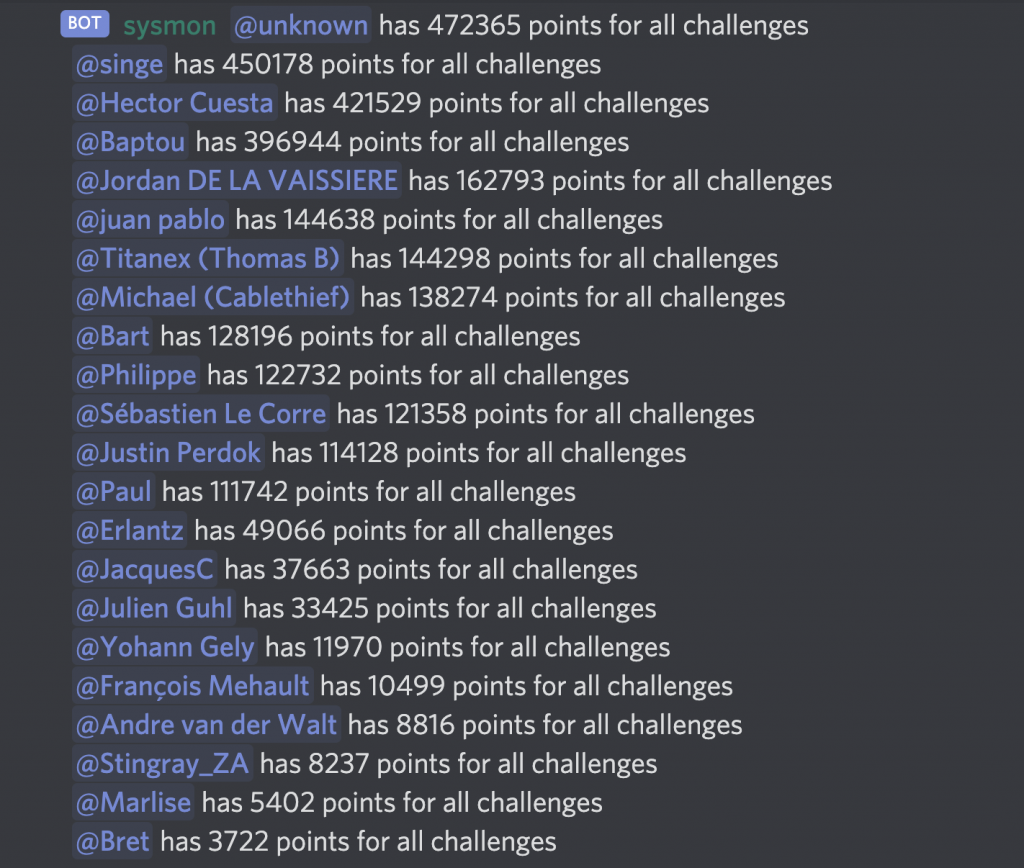
Details on the four password challenges themselves will be revealed in a followup blog post!
sconwar programming challenge
The second challenge was a programming challenge. What could be seen as a little left-field for a hacker conference, I believe it’s super important to understand the technologies that we hack daily, and what better way than to write your own game client, consuming a REST-ful API.
Enter sconwar, a turn-based game that exposes a REST API with the main goal being that you can “bring your own client”, writing it in any language you like.
By issuing a series of moves, a player had to move around on a 20 by 20 board, attacking other players / creeps, picking up power ups and ultimately getting the highest score for a game on the scoreboard.
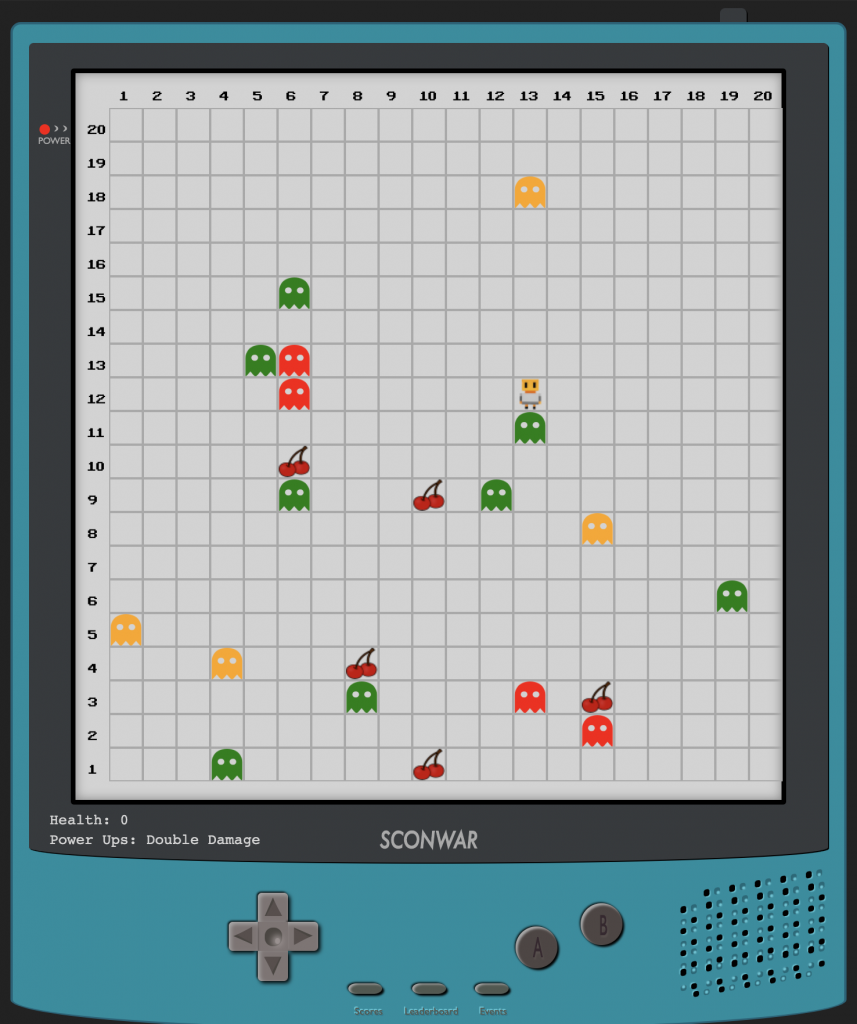
Many clients were quickly whipped up, some of which had early signs of automatic decision making, which was incredible to watch!
discord challenge
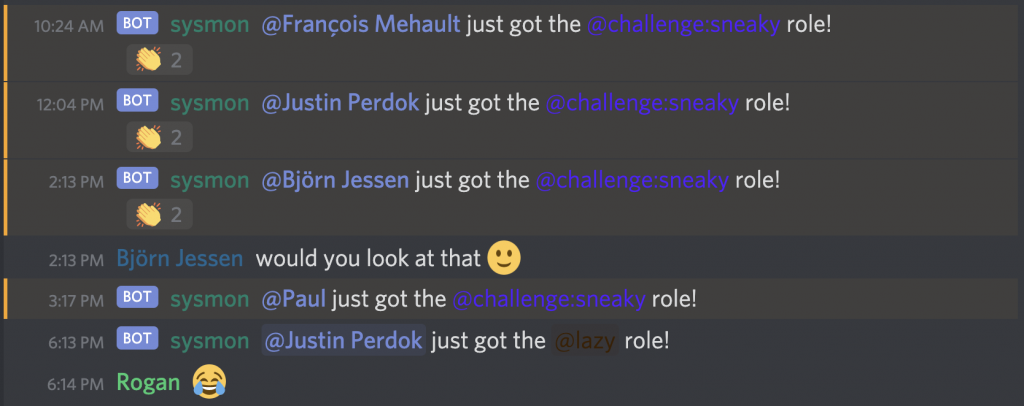
A separate blog post will go into the details of the Discord bot challenge, but the basic premise was that the bot was listening for a number of events, and using the Python bindings, we reacted in certain ways. For example, if someone edited a message, they would get the @challenge:sneaky role. This was the most common role folks got, and also tipped off the crowd that other challenges existed.
hackathon
The main event at Sensecon is the hackathon. There are many reasons it’s run the way it is, but to summarise it, the point is to hack or build something in 24 hours. The hackathon starts on Friday afternoon after a project pitching phase where everyone “sells” their idea that they want to work on. The main aim is to have your idea challenged a little, but also to attract others to form a team.
In total we had nine teams formed, which kicked off the hackathon in the afternoon. Projects worked on ranged from building CI/CD pipelines to automatically scanning payloads used in Red Teams in a fast, reproducible manner, emulating previously vulnerable Router firmware to find new vulnerabilities to patching the official Telegram client to abuse the “Near Me” feature.
Teams primarily used Discord to coordinate efforts. Each team had their own section with a voice and chat channel which worked out great!
Hacking away at projects continued through the night into Saturday where an hour before the official closing time, teams prepared a short 15 minute presentation to show the work they had done. In total, the presentations took ~2.5 hours to work through. It’s amazing to see what hackers can come up with in admittedly not a lot of time, fighting sleep deprivation yet still showing their dedication and excitement towards their cause.
The 10 teams we formed, with the ideas they worked on were:
- Team Red Sparrow PassedLine: Red Team Payload AV evasion CI/CD
- Team HideYoFlag: Jeopardy style CTF building
- Team emulacion-emulation-emulasie: Vulnerable router firmware binary emulation using Qling
- Team Captain Iglo: Phishing infrastructure setup automation
- Team Marrons hachés: Hashcat feature add to crack NetNTLM using NT hashes
- Team pAPI: Build an OWASP Top 10 vulnerable API project
- Team The Badgers: Building short (+-4 hour) short courses
- Team LatridiTeam: Environment variable based LOLBin hunting
- Team Telestalkers: Hacking the official Telegram mobile application to abuse the “Near me feature”
- Team Vulnerable Souls: Build a vulnerable VM
Be sure to watch the blog for details about some of these projects going public soon.
other events
To help with a bit of a mental break (and have some fun), Thursday night was movie night. Relaxing on discord, we watched classics like Hackers & Wargames.
Friday night we had a quiz night. Using Kahoot, a varying set of questions mixed between trivia, general knowledge and other technical questions, hackers had to answer correctly as fast as they could.
At the end of the hackathon, after the project presentations and the final closing ceremony, those that could still keep their eyes open played a few rounds of AmongUs for some relaxation into the rest of the night.
awards
Sensecon also has an awards ceremony! Nominations are solicited from everyone before the conference for one of the following three categories; best hack, best tool and best blooper. Each category had a winner with two runner-ups with some ridiculous hacks taking first place. As for the details, well, you’ll have to be there to know. Hint, we’re hiring! ;)
conclusion
I had a blast, and even though I may be biased, I think our biggest ever, remote Sensecon was a great success. Running conferences remote is hard, like many things people have had to deal with this year. But, if anything, Sensecon has proven that it is possible to run remote, engaging events with people from across the globe.
To next year!


