The slides | tool | paper from BlackHat07/DefCon07 have been posted online for your wget’ing pleasure.
More details on squeeza (the tool) can be found on the squeeza page, but in a nutshell is a sql injection tool that uses Metasploits concept of splitting exploit/payloads/etc with SQL Injection attacks. Current modules are written for MS-SQL server but include functionality for (user defined sql queries, some db schema enumeration, command execution, file-transfer, db_info) and the information is returned (channel selection) via one of (application error messages, DNS, Timing). The modularity’ness means that these all mix and match – I.e. if you write a module to “extract data from all tables that look like username*”, the results would be available on any of the available channels.. (Its a pretty neat tool.. and saved our bacon more than once) So check it out, and send feedback to research@sensepost.com
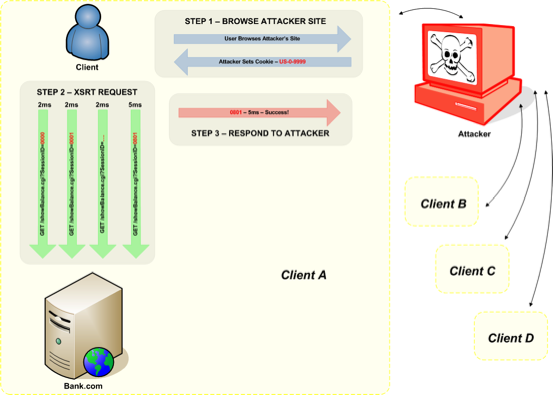
The Paper / Slides (the paper really needs a touch of updating) cover the data exfiltration via DNS/Timing but also goes into a not-so-well-known attack dubbed Cross Site Request Timing. Since page load times (and other page activities) can be timed across the domains it ends up being a nice way to kick the same origin policy in the shins. (we know the world really doesnt need another acronym related to X.S* but couldnt resist!)
If nothing else, in its current guise the attack should let a popular page (one thats been reddit’ed / Slashdotted) make use of its visitors for a distributed brute force attack on web applications that track session-state through the URL/POST body..
Visio pic of the attack in action (courtesy of Nick our Visio Ninja)(click images for full size)
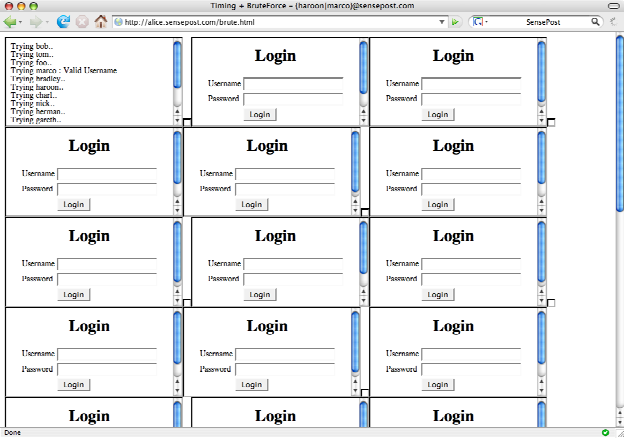
and the example we demo’d during the talk was a brute force attack on a time-leaky login page:
Check out the paper / slides* and send us feedback…
(*Sadly in pdf, the slides do not play our embedded hampster .mp4.. so when u get to slide 40 please surf to http://youtube.com/watch?v=a1Y73sPHKxw )