Wi-Fi is everywhere and having a better understanding of it can fair you well! Over the years we have made various tools such as hostapd-mana to enable attacks against Wi-Fi, and then tools such as berate_ap for those people who don’t want to, or have to, learn how to use hostapd-mana.
In our Unplugged: Modern Wi-Fi Hacking course you will be forced to shun the convenience of automated tools such as berate_ap and get dirty with setting up Access Points and Client configurations in a terminal window to ensure you have a good understanding of what is happening under the hood.
Captive portals
Let’s go through one of the easier course practicals you will be doing in the training; one way to bypass a typical captive portal.
Captive portals are a common way for hotels and restaurants to sell Internet access to customers, controlling who has access while limiting the amount of data they can use. Practically these are often implemented as an open wireless network that when connected to automatically pops up a login screen that requires some sort of information from you.
Given that the lab is all about the command line, the first thing to do is use airodump-ng to see which networks are available around us.
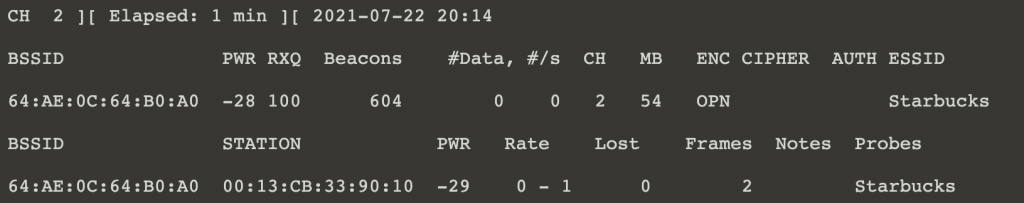
Here we can see an Open network called “Starbucks” (Just thematic, not based on an actual Starbucks) with some clients connected.
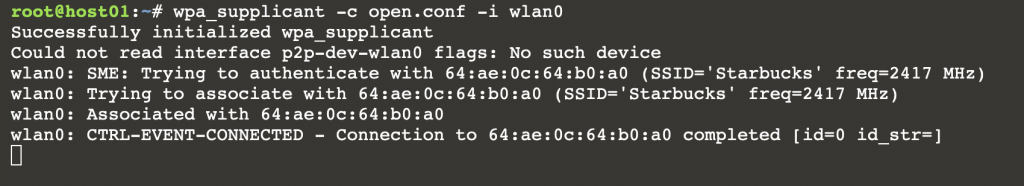
When we try and browse the somewhere on the Internet, we instead get shown a login screen for the network. In the lab we’ll be using w3m to browse the Internet from the command line.
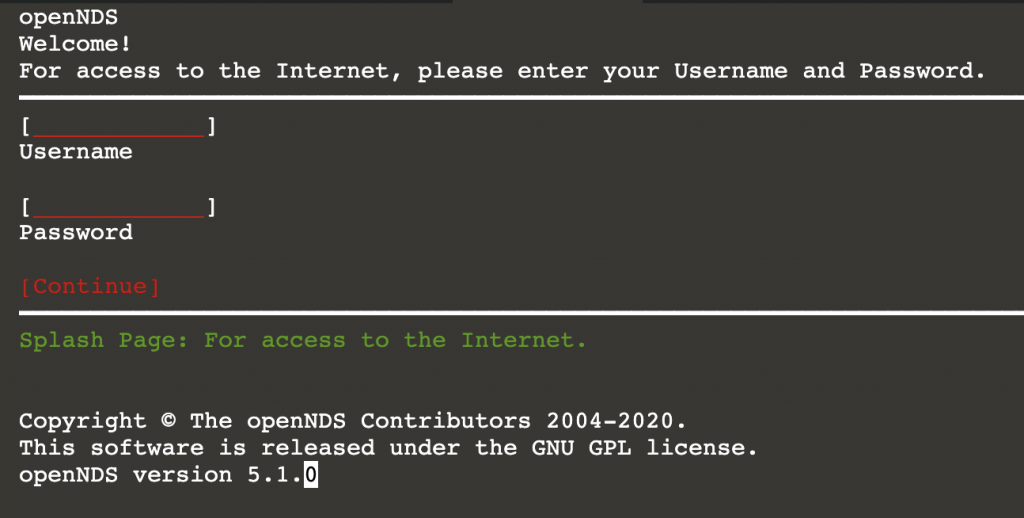
Having been foiled, we start up airodump again and view the connected devices. Given the way Wi-Fi works we get to see the MAC addresses of both the Access Point and Stations (Devices connecting) in our airodump output. This is convenient as the primary way most captive portals work is to redirect unauthenticated users/MAC addresses to a captive portal via some sort of interception. Once authenticated the users MAC address is added to an allowlist, bypassing the captive portal and allowing them to use the Internet normally. The software in use for this in the example is OpenNDS which is a very popular implementation.
Given that we can see the MAC addresses of devices connected to the Access Point and we have full control over our own device, it is possible to set our MAC address to mimic another device and connect. This will trick the Captive portal software in thinking that we are a different user that has already authenticated, allowing us through. We pick a victims MAC address from the output and using macchanger (an easy way to change your MAC address), we mimic that address which may be an already authenticated user. Keep in mind, at this point if that user had paid for Internet we would be stealing that data as we would be pretending to be them.
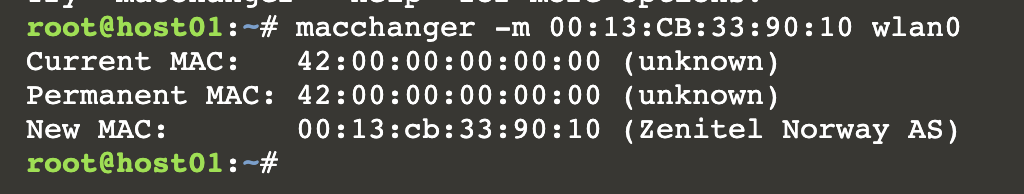
Now when we try and access the Internet, we’ll be allowed through, effectively bypassing the captive portal by impersonating another user.
Hopefully you enjoyed this simplified walk through of the one of the practicals in the course, and it helped you to understand some of how this popular implementation may be easily circumvented.
What’s in the course?
Using various tools and techniques we walk through the basics of “What is a Wi-Fi”, “How to steal your neighbours Wi-Fi”, “How to abuse the local coffeeshop’s Wi-Fi”, and “Why you should not do the previous two learnings”.
We further explore “Attacking corporate Wi-Fi setups”, “Attacks against corporate clients”, and “Relaying credentials to get you onto the Wi-Fi”. Finally, we round it off by going over some of new protocols such as WPA3 and what we can do with them.
By learning how to attack wireless networks, technologies and configurations you also learn how to defend against these attacks, as knowing what stands in your way also gives you the knowledge to get in attackers’ ways.
Who it’s for?
This course is ideal for:
- Those wanting to better defend against Wi-Fi attacks
- Those looking to increase their Wi-Fi attacking skills
- Those curious about what Wi-Fi is and how to abuse it to their liking
Tools needed?
All the tools used in our course are open source and the lab environments are entirely online using the very convenient mac80211_hwsim which allows for the emulation of wireless devices in the cloud. This means that you do not need to bring any hardware and can practice in the safety of your own browser. We’ll provide you with all the tools and techniques to ensure you are well set up to take home all the skills you’ve learned.
The end result?
Hopefully after the training you should have a better idea of how Wi-Fi and the various tools to attack it works.
Join us!
For more practicals and theory please join our Unplugged:Modern WiFi Hacking course at Black Hat USA 2021.
For more information or too book your seat visit: https://www.blackhat.com/us-21/training/schedule/index.html#unplugged-modern-wifi-hacking-22022


