In a world of returning back to, well, “normal” it meant that we could finally have our annual internal hackathon as Orange Cyberdefense in person! And that is exactly what SenseCon 2022 was. An internal, global ethical hacker conference spread across six regions. In this post we’ll talk about exactly that, the challenges as well as the projects people worked on.
As a bonus, we have one of the challenges, BuzzWord, available for you to play via our Discord server, today! Just join using this link, and check out the instructions in the #buzzword-instructions channel.
hackers! with legs!
Like previous years, we had training, some challenges for people to play, a quiz night, a 24 hour hackathon and a social event on the last day in each region. Everything was organised via Discord, however with the in person nature of the event it was mostly a platform to broadcast messages and organise ourselves.
Without a doubt, the highlight of this year’s conference was the ability to travel and meet hackers from other regions.
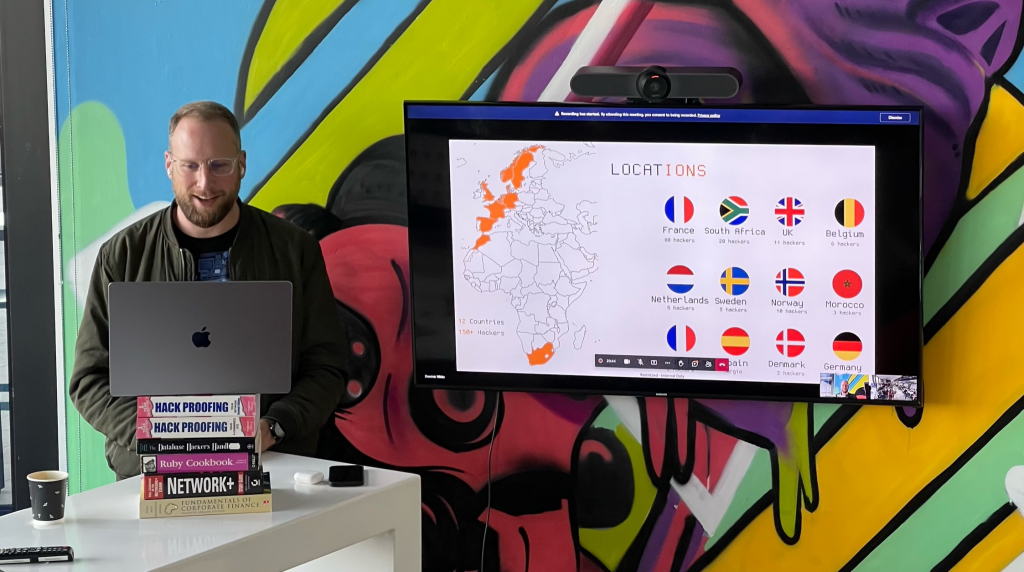
The following regions either received hackers and or sent hackers elsewhere; France, Norway, South Africa, Sweden, Belgium, Netherlands and the United Kingdom. In contrast to previous, remote only events, the in-person interactions resulted in a huge amount of energy buzzing in the office which is quite something to experience. In some regions no opportunity was spared for some local hospitality too!

challenges
This year there were two challenges. Fewer than last year, but that’s okay, we wanted to hang out more while hacking! The challenges we had were a password challenge built by Bart van Bodegom and an interesting optimisation challenge by Dominic White. Both challenges were integrated with discord where we had both scoreboards and automatically assigned roles depending on your challenge progress.
If you are keen to see how we’ve built these features before, you can have a look at the code for last year’s challenges in this Github repo. This year we followed the same pattern.
password challenge
Bart’s password challenge proved to be a challenging one, but well received! Through a narrative, available on Github for you to play if you’d like, a series of three password cracking challenges were built.
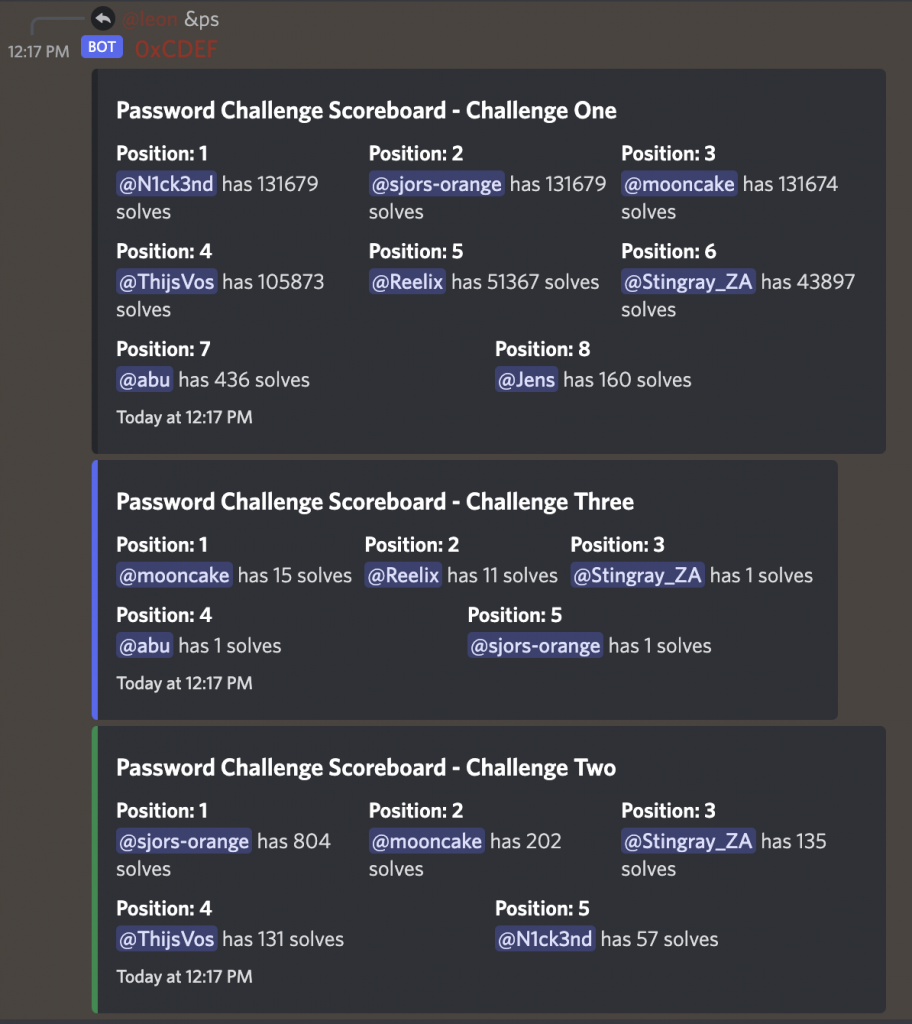
There are still some hashes that have gone uncracked!
optimisation challenge
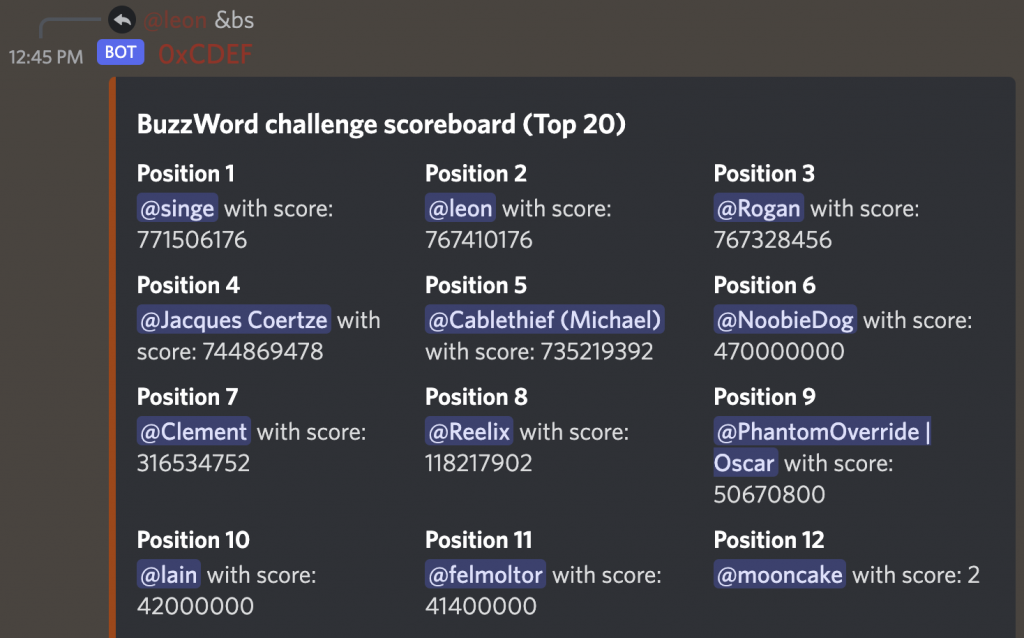
Titled “BuzzWord”, Dominic’s challenge had us test our understanding of some of our favourite programming languages (and in some cases the laws of physics ;) ) in a race to submit the most “FUD” to the server. This challenge is available for you to play as well, today, with all of the instructions available on the OCD Discord server here, detailed in the #buzzword-instruction channel.
training
Four training sessions were run with participants from all of the regions. There were some strong themes as well, with two workshops specifically tackling Infrastructure as Code and automation using Ansible and Packer. Then we also had a mobile hacking workshop and an Ethereum / Smart Contract / Solidity workshop. These workshops were all delivered by the same hackers that perform security assessments professionally as part of their day job. The workshops given were:
- CryptBoot by Jacques Coertze – A cryptocurrency workshop focussing on Ethereum, this practical workshop covered Ethereum basics, smart contract development, dApps, transaction costs and finally the types of vulnerabilities you can find.
- Infrastructure as Code (Ansible) by Justin Perdok – A workshop intended to bootstrap folks in using Ansible to quickly develop and deploy reproducible infrastructure. The workshop covered Ansible Ad-hoc tasks, playbooks and roles delivered via multiple practical exercises.
- Infrastructure as Code (Packer) by Jason Spencer and Darryn Cull – Another infrastructure as code session that focused on using Packer as a means of building reproducible images (mainly in AWS, but it’s not limited to that). The workshop covered all of the tools you’d need to get started, how to run provisioners such as Ansible and more.
- Mobile Hacking by William Vermaak – Focusing on Android for the session, the workshop covered both a practical setup for hackers to be able to intercept and reverse engineer mobile applications as well as some example vulnerabilities to find.
hackathon
Arguably the most exciting activity at SenseCon, the hackathon is a 24 hour session where we organise ourselves into teams and go away to build / break things. It comes with a bit of pre-planning in the days leading up to SenseCon, but once the hackathon starts we have a good idea on which projects to work on.
This year we had 16 teams, and a short summary of the projects the teams worked on follows. Be sure to watch the blog as more detailed posts for some of these projects go public in the coming months!
project: moar c2
This project explored the potential of using Microsoft Teams as a Command and Control channel. While using the Microsoft Graph API is a common method to access Microsoft Cloud services, this project focussed on replicating HTTPS communication just like a Microsoft Teams client would have while integrating it with Cobalt Strike’s ExternalC2.
project: goout mobile
Egress busting using services such as http://letmeoutofyour.net/ and http://allports.exposed/ is a useful way to check that you have outbound connectivity. A tool such as go-out provides a simple scanning interface leveraging those services. This project aimed to build a mobile version of go-out, together with a service that could be triggered via the discovered open port to open say a VPN or similar.
project: red teaming – initial access
This project aimed to develop some more initial access vectors ideally for use in phishing during Red Teaming operations. The team focussed on ClickOnce applications, ISO’s and encrypted ZIP files, and managed to produce two complete scenarios.
project: ics / iot command and control
Leveraging modbus, the team set out to build a Command and Control channel that would look like familiar traffic that one would observe on an OT network. Using the Write Multiple Registers Function (Function 16), the team was able to build a relatively performant Proof of Concept!
project: windows admin centre credential relay
Windows Admin Centre is effectively a web based GUI for Windows Server administration tasks. Relaying credentials using ntlmrelayx was not working, so the goal of this project was to figure out why, and hopefully fix it.
project: wi-fi course infrastructure refresh
We deliver Wi-Fi hacking training in the cloud! This project was a significant effort to move off an older platform that the training was built on into a pure AWS environment. Some of the nuts and bolts had to be rewritten / refactored for that to happen though.
project: osintool
This project focussed on figuring out which open source intelligence tools currently exist, exploring which ones still work well, and seeing how they could be used together. As a Proof of Concept, the team built a pipeline that took a Steam username, and built a relationship view based on their friends, visualised in a Neo4j graph database.
project: hack like mr robot
This project aimed to build a USB device that would form part as a driveby attack to dump hashes from a target Windows computer.
project: keylogger brute force
This team had a hardware key logger that nobody remembered the password to extract recorded keystrokes for. So, using a rasberrypi and some hardware hackery, they set out to build a tool to brute force the passphrase for the key logger.
project: evilnginx automation
Continuing with the strong infrastructure as code theme for this year’s SenseCon, this team set out to build automation to setup and deploy a completely fresh instance of Evilnginx using Terraform and Ansible.
project: telegram anonymous groups
Telegram introduced the ability to anonymously post in Telegram groups. This team set out to test just how anonymous those posts would be, and to search for ways to deanonymise users.
project: pulumi web
Did I mention Infrastructure as Code yet? Not?! With all of the SensePost training labs living in the cloud (even Wi-Fi!), we’re always experimenting with making that better. This project aimed at taking existing labs based on Pulumi, and building a web interface around it to manage their lifecycle and enable some interesting integrations.
project: wink hub
Having access to a Wink Hub, this team took on the task of jailbreaking the device (albeit successfully too using a glitching technique!) in order to play with the numerous radio interfaces that it has.
project: classic car remote start
Continuing on the hardware hacking train, this team took on the task of making an old 1986 VW Golf start remotely using an ESP-8266 and a smartphone.
project: hive
This team took on the task of getting an instance of MediaCMS up and running for internal video hosting, complete with using S3 for content storage and automating image builds and infrastructure deployment.
conclusion
That was a lot for three days! Training, challenges, a hackathon and more, I can’t wait for next years’ already! Be sure to watch the blog for updates as some of these projects mature into more.


