In a similar fashion to the BlackHat challenge held earlier this year, we’re giving away a free ticket to our BlackOps course at this year’s 44Con. As a penetration tester, knowledge of an issue is not enough when one needs to demonstrate risk to a client. Furthermore, when large numbers of potential targets are involved, it becomes crucial that effective attacks are packaged and automated to allow for mass-pwnage.
During an engagement, you notice that a fair portion of the client’s SIP devices still have the default administrative password set. You’re particularly interested in compromising these devices since they also have an embedded SSH service that can be activated and used to mask your actual position on the network.
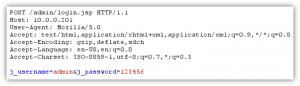
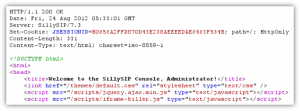
The web-based administration console runs over HTTP (TCP/80) and the default administrative password is 123456. You also notice that a successful administrative login will result in a welcome message within the webpage title.
Figure 1. A HTTP login request to the SillySIP administrative console
Figure 2. A (partial) response, from the SillySIP administrative console, for a successful login
The Challenge:
Leverage the power of Metasploit by creating a Metasploit module to easily scan multiple targets to determine whether the default administrative password is still active on the device.
The Prize:
The first person to send us a working metasploit module (email/twitter) will win a free pass to our training course at 44Con and a limited edition anniversary t-shirt.
Good luck!