This year marks a special anniversary for us at SensePost in that we’ve been training at BlackHat for over a decade now. To celebrate this, we thought we’d give away a free ticket to any of our courses on offer at this year’s BlackHat Briefings in Las Vegas.
This year marks a special anniversary for us at SensePost in that we’ve been training at BlackHat for over a decade now. To celebrate this, we thought we’d give away a free ticket to any of our courses on offer at this year’s BlackHat Briefings in Las Vegas.
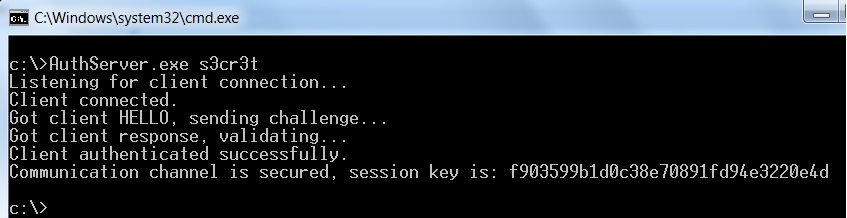
With data breaches happening almost on a monthly basis these days, everyone is turning to encryption in order to protect their information. Bob, a rather tech-savvy gentleman, works for a FTSE 100 company and they’ve written their own secure message implementation. You’ve been tasked to perform a penetration test and noticed that after compromising their shared document server, an internal web application leaked the source code used by the company for the client and the server.
From a cursory glance, Bob is tasked with sending a short message to his office every day over the Internet. The company installed the client software onto his shiny machine and it works by first authenticating him to the server, using a shared secret. The software then allows him to create a message, encrypt it and send it onto the server. As part of the assessment, you’ve compromised a number of servers and are now in the process of intercepting Bob’s network traffic, in order to decrypt his communications.
By observing bob’s password history, you’ve become aware that Bob’s secret key length is 7 characters long, and contains alpha-numeric characters with no upper-case letters.
The Challenge:
The client has been informed of your progress so far and has categorically stated that this encryption method cannot be broken. We want you to prove this to be incorrect by telling us the shared secret and calculating the encryption key (kc), which is used to decrypt Bob’s messages.
The Exfiltrated Files:
The files you will need can be downloaded from here. They include:
- The challenge PCAP file – Please note that the PCAP file only contains the authentication protocol traffic and not the encrypted messages.
- Obtained client/server source files
The Rules:
The first person to correctly send us the shared secret and encryption key (email/twitter) will win a free pass to any of our BlackHat 2012 training courses and a limited edition anniversary t-shirt. You’ll also get to hang out with us at Vegas (worth more than anything we feel!)
Good luck!
Update:
Thanks for all the entries, it’s great to see people enjoying a good challenge. We do have a winner, once he has confirmed how he did it and what course he would like to attend, we will let you all know.